Linux log monitoring for SOC teams is a critical practice in modern cybersecurity. Think of your Linux servers as tireless digital detectives — constantly capturing every action, alert, and anomaly in real time. These digital footprints, known as log files, are far more than technical noise. For a Security Operations Center (SOC), they’re the front line of defense. Logs are the system’s diary — essential for detecting threats, investigating incidents, meeting compliance standards, and even preventing breaches.
In this guide, you’ll learn which Linux log files matter most, how to use them effectively for threat detection, and the best practices for managing logs to ensure visibility, integrity, and compliance.
The Foundation: Centralized Logging
Linux logging has come a long way. While traditional syslog still plays a role, modern systems leverage powerful tools like rsyslog, syslog-ng, and especially journald. Journald is a game-changer, collecting logs in a structured, binary format that makes analysis faster and more efficient. But no matter the format, the goal is the same: get those logs to a central point.
Imagine trying to find a needle in a thousand haystacks. That’s what scattered logs feel like. Centralized logging solves this by pulling all your log data into one place, often a Security Information and Event Management (SIEM) system. This isn’t just convenient; it’s vital for real-time threat detection, allowing your SOC to see across your entire IT infrastructure and correlate events from different systems to spot complex attacks. Tools like the ELK Stack (Elasticsearch, Logstash, Kibana), Graylog, and Splunk are popular choices for this.
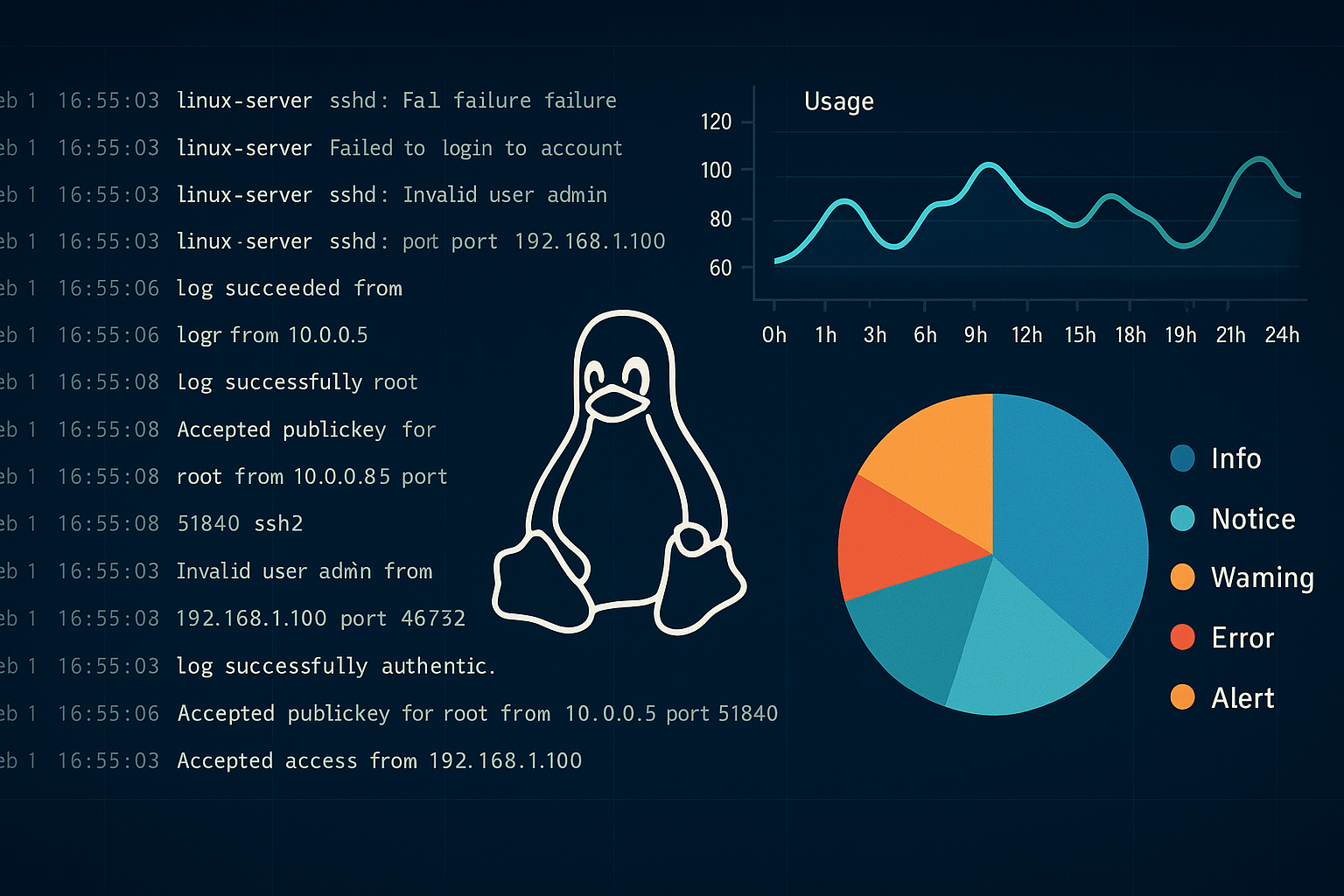
Your Linux System’s Security Diary: Essential Logs for SOCs
Every Linux system keeps a detailed record of its activities. Here are the core logs your SOC needs to monitor:
- Authentication Logs (
/var/log/auth.logor/var/log/secure): These logs are your system’s bouncer, tracking every login attempt—successful or not. They’re crucial for spotting brute-force attacks, unauthorized access, and privilege escalation attempts (likesudousage). - Kernel Logs (
/var/log/kern.log): The kernel log is the heartbeat of your OS, recording low-level system events. Keep an eye out for kernel panics, hardware errors, or suspicious kernel module loads—these can signal deep system compromises like rootkits. - Boot Logs (
/var/log/boot.loganddmesg): These logs chronicle your system’s startup. They’re vital for detecting persistence mechanisms (attackers often modify boot scripts) or tampering with critical system files. Remember,dmesglogs are volatile, so forward them quickly! - Failed Login Attempts (
/var/log/faillog,/var/log/btmp,/var/log/wtmp): Dedicated to tracking login activity, these binary files (lastb,last,faillogare your friends here) are goldmines for detecting brute-force attacks and credential stuffing. - Scheduled Task Logs (
/var/log/cron): Thecronlog tracks all scheduled jobs. Unexpected commands running at odd hours or changes tocrontabfiles are red flags for persistence or malicious activity like cryptocurrency mining or data exfiltration.
Beyond the OS: Application Logs for Deeper Insights
Beyond core system logs, application-specific logs offer crucial visibility into the services and applications that attackers often target:
- Web Server Logs (Apache, Nginx –
/var/log/apache2/,/var/log/nginx/): Your web servers’ access and error logs are critical for catching web application attacks like SQL injection, XSS, directory traversal, and DDoS attacks. They show you who’s hitting your site and how. - Database Logs (MySQL, PostgreSQL –
/var/log/mysql/,/var/log/postgresql/): Databases hold your most sensitive data, and their logs track everything from errors to user connections. Monitor them for unauthorized data access, privilege escalation, SQL injection attempts, and data exfiltration patterns. - SSH Daemon Logs (
/var/log/auth.logor/var/log/secureforsshd): SSH is how you remotely manage Linux systems. Its logs, often part of the authentication logs , reveal successful and failed login attempts, brute-force attacks, and even the creation of covert tunnels for data exfiltration. - DNS Server Logs (BIND –
/var/log/named/,/var/log/bind/): DNS logs record all domain name resolution. They’re surprisingly powerful for detecting Command and Control (C2) traffic, DNS exfiltration, cache poisoning, and network reconnaissance.
Next-Level Logging: Auditd & Journald
Modern Linux environments offer sophisticated logging frameworks for enhanced security:
- Linux Audit System (
auditd–/var/log/audit/audit.log):auditdis Linux’s built-in, kernel-level auditing framework. It captures incredibly detailed, unbypassable information about system calls, file access, and user actions. This makes it invaluable for deep forensic analysis, meeting strict compliance (PCI-DSS, HIPAA, SOX), and detecting advanced threats like rootkits. - Systemd Journal (
journald):journaldissystemd‘s modern logging service, collecting logs in a structured, binary format. This means efficient storage, faster querying, and easier analysis for automated tools. It’s perfect for real-time monitoring and feeding data into your SIEM. - Complementary Power: Think of
auditdas your high-resolution security camera for critical events, andjournaldas your efficient central diary for all system activity. Using both gives you comprehensive visibility for both deep investigations and broad operational awareness.
Compliance Corner: Why Log Retention is Non-Negotiable
Meeting regulatory standards isn’t just good practice; it’s often a legal mandate. Logs are your proof of compliance. Here’s a quick look at key requirements:
- PCI DSS: Requires tracking all access to cardholder data and network resources. Logs must be attributable to a unique user, protected from tampering, and retained for at least one year (with three months immediately available).
- HIPAA: Mandates logging of all activity in systems containing electronic Protected Health Information (ePHI). Logs must be secure and retained for a minimum of six years.
- GDPR: Emphasizes “storage limitation”—don’t keep personal data longer than necessary. While no exact period is specified, common practice suggests 90 days for authentication logs and 1-2 years for security event logs. Focus on data minimization, anonymization, and strong access controls.
- NIST SP 800-53: Requires logging specific event types (authentication, file access, privileged use) and retaining audit records for an “organization-defined time period.” Common practice suggests at least 3 years (90 days hot, 365 days warm).
- ISO 27001: Stipulates that event logs must be produced, retained, and regularly reviewed, and protected from tampering. While no specific period is set, a common rule of thumb is at least three years.
Summary of Log Retention Requirements by Compliance Standard
| Compliance Standard | Minimum Log Retention Period | Key Logging Requirements (Summary) |
|---|---|---|
| PCI DSS | 1 year (3 months immediately available) | All access to CHD, admin actions, invalid logins, authentication changes, log clearing. Attributable to unique user. Protected from tampering. Accurate timestamps. |
| HIPAA | 6 years | User activity (who, what, when), database changes, new users, access levels, file access, OS logins, firewall, anti-malware. Protected from alteration/deletion. |
| GDPR | “Reasonable period” (e.g., 90 days for auth, 1-2 years for security events) | Data minimization, anonymization/pseudonymization, access controls, encryption, audit trails for log access, transparency, user rights (erasure). |
| NIST SP 800-53 | Organization-defined (commonly 3 years; 90 days hot, 365 days warm) | Authentication events, security-relevant file/object events, user/group management, privileged use, system changes. Includes event type, time, source, user. |
| ISO 27001 | Organization-defined (commonly 3 years) | User activities, exceptions, faults, info security events, system config changes, privilege use, file access, network details. Protected from tampering. Clock synchronization. |
Supercharging Your SOC: Best Practices for Linux Logs
Effective log management goes beyond just collecting data. Here’s how to make your logs a powerful shield:
- Centralize & Aggregate: Don’t let logs live in silos. Use a SIEM (like ELK, Graylog, Splunk) to pull all logs into one central repository . This gives you a unified view and simplifies management.
- Normalize & Enrich: Raw logs are messy. Transform them into a consistent format (normalize) and add context (enrichment) with threat intelligence or asset data . This makes detection much more accurate.
- Correlate & Alert Smartly: Link events from different sources to spot complex attack patterns. Tune your alerts to minimize false positives and prevent ‘alert fatigue’ among your analysts.
- Tiered Storage & Retention: Balance compliance and cost with a tiered storage strategy (hot, warm, cold) and clearly defined retention policies.
- Protect Log Integrity: Logs are evidence. Protect them from tampering with immutability, strong access controls, and encryption . Forward them to a secure, off-host location .
- Map to MITRE ATT&CK: Align your detection and response efforts with the MITRE ATT&CK framework . This helps you understand adversary tactics and prioritize your defenses.
- Continuous Improvement: The threat landscape is always changing. Regularly review your logging policies, update detection rules, and test your incident response plans to stay ahead .
Your Logs: A Powerful Shield
Linux logs are more than just technical records; they’re a powerful cybersecurity asset. By understanding which logs to monitor, leveraging advanced tools like auditd and journald, and adhering to compliance mandates, your SOC can transform raw data into actionable intelligence. Embrace centralized logging, smart correlation, and continuous improvement to build a resilient defense against evolving cyber threats.










Alright fellas, been spinning the reels a bit over at taib29bet. Pretty decent selection, nothing too crazy but keeps you entertained. Wouldn’t mind seeing some more promotions though, ya know? Check it out here: taib29bet
Downloaded the qk777gameapk today and so far, so good! Installation was a breeze, and the games are kinda addictive. Give it a shot if you’re into mobile gaming! qk777gameapk
007gamecasino… Okay, the name definitely caught my attention, haha. Felt like I was on a Bond mission spinning those slots! Fun experience, worth a shot! 007gamecasino
Looking for the RP777 game APK. This site seems to have the goods. Just gotta make sure it’s legit before I download. Fingers crossed! rp777gameapk
Yo, gameb369 is my go-to spot. Seriously, if you’re looking for some fun and maybe even a little win, check it out at gameb369. Good times.
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me? https://www.binance.info/register?ref=IHJUI7TF
Easy peasy login process at CK777login. No need to jump through hoops, which is a big plus in my book. Time to win some moolah! Check login at ck777login
Downloaded the jiliappcom app and I gotta say, it’s pretty smooth. Easy to find what you’re looking for, and the games load quickly. No annoying lag or glitches so far. Definitely a must-have for mobile gaming! Get the app here: jiliappcom
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article. https://www.binance.com/si-LK/register?ref=LBF8F65G
89betvip… hmm, feels like a newbie on the block. Interface is pretty clean, but need more game variety to compete. Worth a peek if you’re bored though. See what you think: 89betvip.
Okay, aaajlcasinolegit are they for real Legit I say Always double-check before throwing your money around, yeah Find out more at aaajlcasinolegit.
ABC8viplogin, alrighty then. It looks fairly standard to me. Login is straightforward I guess. If you’re curious, here’s the link abc8viplogin.
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me?
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.
Your point of view caught my eye and was very interesting. Thanks. I have a question for you.
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.