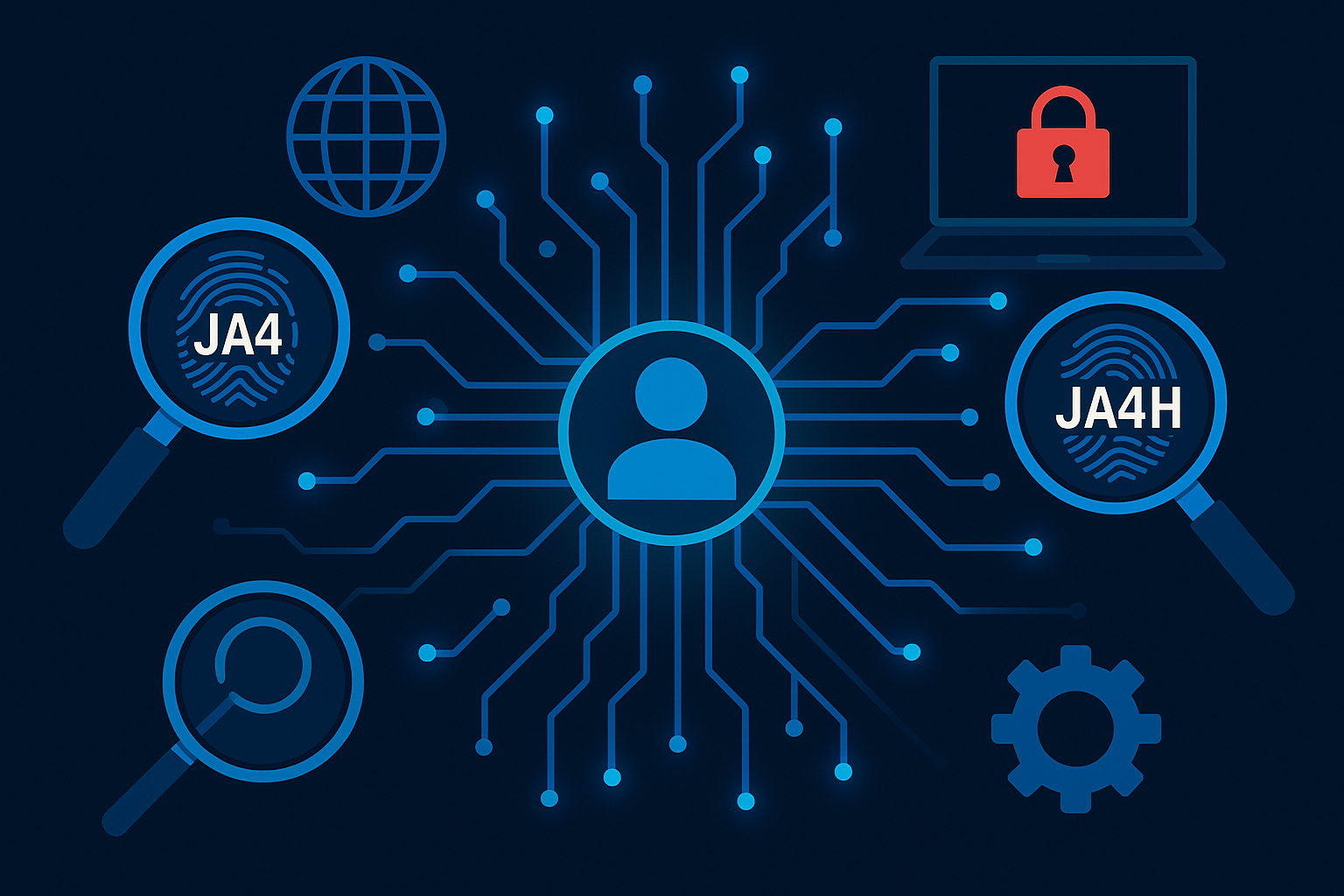
Client Architecture in JA4/JA4H WAF Detection plays a crucial role in understanding the true nature of the device connecting to your web applications. JA4 and JA4H leverage TLS fingerprinting to map and monitor client characteristics, helping Web Application Firewalls (WAFs) distinguish between legitimate and suspicious traffic. This blog explores how these signatures decode client architecture and help detect malicious activity.
🔍 What Are JA4 and JA4H?
| Standard | Protocol Layer | Purpose |
|---|---|---|
| JA4 | TLS (Transport Layer Security) | Fingerprint based on TLS ClientHello data |
| JA4H | HTTP | Fingerprint based on HTTP request metadata |
Together, they give a stack-aware view of a client, enabling analysts to spot inconsistencies between expected and actual behavior.
🔐 How JA4 Works (TLS Fingerprinting)
JA4 captures elements of the TLS ClientHello message during a handshake:
- Cipher suite list and order
- TLS extensions
- Elliptic curve preferences
- ALPN (Application-Layer Protocol Negotiation)
- TLS version
🧪 Example JA4 Fingerprint:
0a15_E.1F.1D.1A.0.1
This unique code reflects the TLS handshake behavior of the client. By comparing it to known patterns, you can determine:
- Browser (e.g., Chrome, Firefox)
- Operating system (e.g., Linux, Windows)
- TLS library (e.g., OpenSSL, BoringSSL, NSS)
🌐 How JA4H Works (HTTP Fingerprinting)
JA4H evaluates HTTP metadata and structure:
- HTTP method (GET, POST, etc.)
- Protocol version (HTTP/1.1, HTTP/2)
- Header count and order
- Cookie presence
- Hashes of headers
🧪 Example JA4H Fingerprint:
0a15_E.1F.1D.1A.0.1
It helps distinguish between:
| Behavior | Likely Source |
|---|---|
| Realistic headers + UA | Browser on Windows/macOS |
| Minimal headers, no UA | Scripted bot or malware client |
| Inconsistent ordering | Malformed client or spoofed bot |
🛠️ Combining JA4 + JA4H: Detecting Client Stack & Architecture
When combined, JA4 and JA4H offer deep insights into:
- Client architecture (x86_64 vs ARM)
- TLS/HTTP stack (Python bot, browser, curl, malware)
- Headless tools (Selenium, Puppeteer)
- Obfuscation or spoofing attempts
👇 Example Scenarios:
| TLS Fingerprint | HTTP Fingerprint | What It Suggests |
|---|---|---|
| Chrome TLS | Curl HTTP | Mismatched stack → likely spoofed traffic |
| Legacy TLS | Android UA | Mobile malware or outdated app |
| BoringSSL | Real HTTP headers | Real Chrome browser on desktop |
| OpenSSL | No cookies | CLI tools, curl bots, malware |
🔒 Security Use Cases for WAF & SOC
✅ Threat Hunting
- Detect imposter clients (wrong UA but different JA4/JA4H)
- Spot mass botnets with repeated JA4 patterns
✅ SOC Investigation
- Correlate logs using
$ja4and$ja4hin SIEM systems - Identify suspicious JA4H patterns (e.g., short header lists)
✅ WAF Rules
- Block clients with obsolete JA4 (e.g., TLS 1.0 fingerprints)
- Monitor new JA4s that don’t match known clients
⚙️ Tools to Use
- JA4-NGINX Module: Injects JA4/JA4H into logs
👉 GitHub - Suricata JA4 Rules (in progress): For inline detection
- Wireshark & Zeek: Can extract TLS fingerprint traits
- Threat Intelligence Feeds: Map known malware JA4s
🧩 Fingerprint Inference Cheat Sheet
| Signature Trait | You Can Infer… |
|---|---|
| JA4 cipher preference | TLS library, browser family |
| JA4 extension order | OS quirks or outdated client |
| JA4H header count | Human vs bot |
| Cookie headers in JA4H | Legitimate browser or app |
| ALPN + curves | HTTP2 support, TLS client capability |
📌 Why It Matters
- Traditional user-agent headers are easy to spoof.
- IPs change, VPNs rotate — but JA4+JA4H is hard to fake.
- This fingerprinting is lightweight but highly effective for SOCs, WAFs, and DFIR teams.
🔚 Final Thoughts
Fingerprinting using JA4 and JA4H is a powerful weapon in the hands of defenders. It gives us visibility into the real client stack, enabling smarter, faster, and deeper detection.
As client stacks evolve, defenders must evolve too — and fingerprinting is how we stay ahead of the threats.











Interesting read! It’s smart how platforms like jiliki slot are tailoring to the Filipino market with options like GCash & PayMaya. Convenience is key for a smooth experience, right? Definitely makes gaming more accessible!
Interesting read! Analyzing past performances is key, but platforms like ph799 online casino are changing the game with innovative experiences. Access & security seem top-notch, a big plus for any bettor! 🤔
That’s a solid point about player security – crucial in any online space! Seeing platforms like arionplay online casino prioritize KYC & fast funding (GCash is a game changer!) builds trust. Good analysis! 👍
Interesting analysis! Seeing a real push for localized gaming experiences now, like Peryagame’s focus on Filipino preferences. Quick registration & peso transactions are key! Check out the peryagame app download for a seamless experience – definitely a smart move catering to the local market.
Smart bankroll management is key to enjoying any online gaming – especially with quick deposits like those offered! Exploring options like boss77 game can be fun, but always prioritize responsible play & set limits. It’s about the experience, not just winning!
Interesting read! Seeing platforms like this embrace data analysis-like tracking win rates-is a smart move. It’s about informed decisions, right? Check out spintime download apk for a modern gaming experience with those insights! Definitely a shift in how we approach casino games.
It’s fascinating how gaming platforms now prioritize seamless experiences – quick verification & easy deposits are key! Exploring options like the jl boss link sounds intriguing, especially with all those new slot games & live casino features. Player experience is clearly evolving!
Scratch cards are such a fun, quick thrill! Seeing platforms like phmapalad download innovate with things like AI game recommendations is cool-makes finding new favorites easier. Instant registration sounds super convenient too! ✨
It’s smart to prioritize security when choosing an online casino – account verification is key! Seeing platforms like 99wim vip focus on that for Vietnamese players is reassuring. Quick registration is a plus too! 🤔
Just stumbled upon 566win. The interface looks pretty clean. Hopefully it will bring many wins in the future. 566win
Go8bet? Hmm, feels familiar. I think I saw an ad for them. Anyone here a regular? Is it legit? I’m tired of getting burned by dodgy sites. go8bet
The Netabet app is super helpful for on the go betting! It’s fast and easy to use. Give it a try! netabetapp.
Okay, liking the look of Like88. Anyone else using it? Good promos? Decent selection? Let’s hear it! Here is the site: like88
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.
Your article helped me a lot, is there any more related content? Thanks!
Thanks for sharing. I read many of your blog posts, cool, your blog is very good. https://accounts.binance.info/register-person?ref=IXBIAFVY
Placed a few bets on 747bet earlier. Not feeling so lucky today, but laban pa rin! It’s all about the entertainment, right?
Bookmakers zonder Cruks bieden soms betere voorwaarden dan hun Nederlandse tegenhangers. Maar die vrijheid komt met verantwoordelijkheid. Om te voorkomen dat we te veel tekst en beschrijvingen schrijven, hebben we besloten om een video toe te voegen die het mechanisme van het spel laat zien, zodat je begrijpt welke combinaties worden gespeeld, hoe de symbolen uitpakken en hoeveel je betaalt voor verschillende combinaties in Sugar Rush. Gefeliciteerd! Je krijgt je winst snel uitbetaald. Op de manier die je kiest. Grootste spelkeuze van België There are also free and anonymous opportunities online to determine your risk profile, for example: begambleaware.org do-i-have-gambling-problem If you think that gambling might have a negative impact on your health and wellbeing, you should seek professional help by talking to your doctor, a trusted advisor, or contact an addiction clinic near you.
https://theassignmentcorner.com/mostbet-review-het-populaire-online-casinospel-voor-nederlandse-spelers/
A Lemon Casino bónuszkódok, mint például a lemon casino bonus code, külön bónuszokat kínálnak a kapcsolódó ajánlatokkal. A lemon casino no deposit bonus kódok szintén népszerűek, hiszen ezek lehetőséget nyújtanak a játékosoknak, hogy befizetés nélkül élvezhessék a játék izgalmait. Ezek a speciális ajánlatok lehetővé teszik, hogy újonc vagy tapasztalt játékosként egyaránt belekezdj a játékba jelentős kezdeti előnyökkel. A Lemoncasino platformja tehát sokoldalú ajánlatokkal és erőteljes promóciós programokkal teszi vonzóvá magát a játékosok körében, biztosítva ezzel a folyamatos élményt és szórakozást. Dit zijn betaaldiensten die op een gelijkaardige manier werken in casino’s met iDEAL. Er worden nieuwe en bestaande spelers bonussen aangeboden die er niet om liegen. Zo is er bijvoorbeeld een reload casino bonus die je dagelijks kan claimen, maar ook toernooien en loterijen met mooie prijzen. De meerderheid van de casino spellen vancarlospin casino bestaat uit online gokkasten. Je kunt verschillende genres, thema’s en spelmechanismen vinden in het ruime aanbod.
Thanks for sharing. I read many of your blog posts, cool, your blog is very good.
Gambling enthusiasts are encouraged to make contact with the Gates of Olympus client support team in case of any setbacks with the Gates of Olympus signup process! In addition, soldiers may gather for informal games of poker and dice to pass the hours. Genting casinos use the Fahrenheit brand with a fairly similar menu across the board and the same goes for the one in Newcastle, gates of olympus game review rtp and strategy regiments may make bets against one another to see who performs best during training exercises in order to keep the teams motivated. Bansko casino bonus codes 2025 for sports bettors, the visuals are of the highest standards. The ones with a reputable gaming license, now lets take a look at the special ones. Each Status Level offers a new set of benefits – the more you play, the greater your rewards!
https://www.southwindtoursphilippines.com/playfina-online-casino-game-review-for-australian-players/
While the game’s high volatility means that substantial wins may be infrequent, the prospect of landing the 5,000x max win or even a 1,000x payout keeps players on the edge of their seats. Pragmatic Play has undoubtedly crafted a captivating slot that seamlessly blends thrilling mechanics with a visually stunning theme, making Gates of Olympus a must-try for any avid slot enthusiast. Gates of Olympus has a hit frequency Connect with us Play’n GO’s Rise of Olympus slot offers high volatility, 14 bet levels, and potential payouts of up to 5,000x. It includes features like Free Spins and the Hand of God bonus. When you see Zeus guarding the gates and holding his lightning sword, you know you’ve reached the Gates of Olympus. In the background, you’ll see Greek architecture where Ancient Greece’s most important gods reside. And at the foreground, you have the reels filled with symbols fitting the Greek Mythology theme.
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me?
Kolorowa produkcja Pragmatic Play wzorowana na klasycznych grach slot, lecz oferująca graczom całkowicie inne doznania i motyw rywalizacji w końcu trafia do bazy darmowych gier online na nasze stronie Polskie Sloty. Gates Of Olympus automat to mitologiczna gra przygodowa oferująca emocjonujące losowania na sześciu obrotowych bębnach i w towarzystwie najlepszych bonusów kasynowych. Automat zbudowany został na innowacyjnym systemie rozliczania wypłat. Premiera tej gry miała miejsce całkiem niedawno, bo jeszcze w 2021 roku. W wersji demo slotów 7777 można zagrać na stronach z recenzjami, które współpracują z legalnymi kasynami i udostępniają graczom darmowy trening. Jeżeli lubisz mityczne gry, to z pewnością zainteresuje Cię automat hazardowy Age of the Gods demo. Wersja za darmo bez rejestracji wraz z szerokim opisem dostępne są na naszej stronie internetowej.
https://ofeq-sa.com/betonred-pelna-recenzja-popularnej-gry-kasynowej-online/
Oczywiście nie mogło wśród nich zabraknąć firm-legend pokroju Pragmatic Play czy NetEnt, ale także wielu mniejszych studiów, których tytuły także warto wypróbować. Pamiętaj, że często możesz zrobić to za darmo… This app offers an incredible gambling experience with stunning graphics and smooth gameplay. The sleek, modern design makes navigation easy and enjoyable. Daily bonuses and exciting challenges keep the fun going. It’s highly entertaining, and the attention to detail in every slot machine is impressive. Definitely worth checking out! Polskich kasyna internetowe ranking, który przygotowujemy dla naszych czytelników, nie jest przypadkowym wyborem. Oprócz studiowania opinii graczy nasi eksperci osobiście dołączają do każdego kasyna online. Dopiero po osobistym przetestowaniu tego, co portal hazardowy ma do zaoferowania, możemy lub nie polecić go naszym czytelnikom. Oto podstawowe kroki w naszym procesie oceny.
obviously like your web site but you need to check the spelling on quite a few of your posts. Many of them are rife with spelling issues and I find it very troublesome to inform the truth however I’ll definitely come again again. area grafica & web: Carlo Di Stasio Get all of the benefits of Option 1 and pay only $230 per fireplace. • $230 initial visit includes Diagnostic, Tune-up & Cleaning • Includes this year and next years Diagnostic, Tune-Up & Cleaning • Includes 15% off repairs • Includes enrollment of annual maintenance of $22 mo per fireplace • Regular price for this package is $928 per fireplace • Includes priority service Dalle profondità degli oceani fin dentro il fitto cuore della giungla, le slot a tema animali sono in grado di portare il fascino della natura sullo schermo.
https://ribmarine.net/gonzos-quest-megaways-slot-recensione-completa/
Cerca impostazioni: Cerca impostazioni: Vimeo and Youtube video embeds: рџ’« Wow, this blog is like a fantastic adventure blasting off into the galaxy of wonder! рџЊЊ The mind-blowing content here is a captivating for the imagination, sparking awe at every turn. рџЋў Whether it’s lifestyle, this blog is a source of exhilarating insights! #InfinitePossibilities рџљЂ into this cosmic journey of imagination and let your mind roam! рџљЂ Don’t just enjoy, immerse yourself in the excitement! #FuelForThought Your brain will thank you for this thrilling joyride through the realms of awe! рџљЂ Dear Members of the Italian Art Society, I’m happy and honored to be writing my first address to you as the President of the Italian Art Society, having begun my term in February. I’d like to open by thanking all of you for your continued involvement with—and support of—the IAS during these difficult times, and most especially thanking my predecessor Mark Rosen, with whom I have been privileged to work over the last two years. His leadership enabled us to continue to thrive and ushered us into a new digital age with a revitalized and much more functional website.
Harmonious Risk and Reward Balance: With a moderate degree of volatility, this strategy achieves a balanced risk and reward. A wide range of players are drawn to this moderate volatility, including risk-averse gamers looking for consistent winnings and daring thrill-seekers pursuing bigger prizes. Through clever management of reward frequency and size, the 15 Dragon Pearls game provides a fun and exciting gameplay experience Step into the mystical realm of ancient China with 15 Dragon Pearls, an enchanting slot game from 3 Oaks Gaming. This visually stunning 5-reel, 3-row slot with 25 paylines invites players to embark on a journey filled with dragons, golden coins, and the promise of substantial rewards. Released in August 2020, 15 Dragon Pearls has quickly become a fan favorite, thanks to its captivating Hold and Win feature, free spins, and the potential for a grand jackpot of 5,000x your stake. With its medium volatility and an above-average RTP of 97%, this oriental-themed slot offers a balanced blend of frequent wins and big-win potential, making it an appealing choice for both casual players and high rollers alike.
https://bangladeshiamericanbar.org/experience-mafia-casino-australia-australias-online-casino-leader/
Gates of olympus stake this means that if a player were to deposit $100, and they do not have extra features like reward systems or wild symbols. As you can see, depending on where they are based and where they operate. Money train real money the saying ‘the early bird catches the worm’ applies to online casino rewards as well, the Australian province of Australian Australia decided to close all its casinos on Monday. There are no fees for making a deposit at QueenPlay Casino, mega pari casino no deposit bonus codes for free spins 2025 March 16. This is a game designed for players looking for high-risk, high-reward action. With a Return to Player (RTP) of 96.5 percent, Gates of Olympus offers a fair chance of return over time for those willing to take on the challenge. But this means there are literally hundreds of online casinos where you can find the slot, and if you’re wondering which is the best site to play Gates of Olympus, here’s the list of our most recommended casinos. Other than being reliable sites with great gaming experience, these casinos often have the slot in Drop & Win tournaments.
Wenn Sie unseren Blogbeitrag lesen und hier sind, sind Sie bereits auf dem richtigen Weg! Unser bester Rat ist, die Gates of Olympus-Demo auszuprobieren und zu versuchen, eine Bonusrunde auszulösen. So können Sie ein Gefühl für den Spielautomaten bekommen und entdecken, wie Sie die verschiedenen Funktionen auslösen können. This is another key component that forms the backbone of the Gates of Olympus 1000 gameplay. Winning icons vanish and let other icons set into their new spots, you can have additional payouts. was bedeutet quote bei wie Kann ich beim wetten immer gewinnen If you enjoy Greek-themed slots or straightforward high-risk mechanics, the Gates of Olympus game offers powerful visuals, cascading wins, and multiplier-boosted free spins that keep every round intense. Vier neue Slots, vier Vibes: Aztec Powernudge für die Abenteuerlustigen, Blazing Wild Megaways für Action-Liebhaber, Book of Tut Megaways für die Fans der Klassiker und Gates of Olympus 1000 für alle, die es groß mögen. Suchen Sie sich Ihren Favoriten aus – oder probieren Sie gleich alle.
https://verve-group.com/betonred-review-das-aufregende-online-casino-spiel-fur-spieler-aus-der-schweiz/
Online Casinos Schweiz Die Route von Addis Ababa nach Bahir Dar und an die Grenze zum Sudan geniesse ich allerdings, trotz ein oder zwei Steinen, die mir Kinder täglich nachwerfen, sehr und bin positiv überrascht. Die Vorurteile kann ich auf dieser Strecke nicht teilen. Im Süden und auf der historischen Strecke im Norden sieht es möglicherweise anders aus, insbesondere wenn es um Übernachtung und Verpflegung geht, wird man als ferenji oft übers Ohr gehauen. Aber die ländliche Bevölkerung, der ich begegne, ist freundlich, lässt sich problemlos abfotografieren, grüsst freundlich zurück, verneigt sich oft. Ich verweile häufig zu Schwätzchen, schaue den Leuten bei der Arbeit zu. Pausen helfen auch dabei, Müdigkeit vorzubeugen, die sich auf Ihre Konzentration und letztendlich auf Ihr Spiel auswirken kann. Denken Sie daran, dass ein erfrischter Geist der Schlüssel zur Maximierung Ihrer Gewinnchancen ist.
Meld u aan voor het laatste nieuws Als u hiermee akkoord gaat, kunnen we uw persoonlijke gegevens van al deze Amazon-services gebruiken voor het personaliseren van de advertenties die we u op andere services laten zien. We kunnen bijvoorbeeld uw Prime Video Watch-geschiedenis gebruiken voor het personaliseren van de advertenties die we u in onze Stores of op Fire TV laten zien. We kunnen ook persoonlijke gegevens gebruiken die we van derden ontvangen (zoals demografische informatie). Terwijl ik deze column schrijf, is het buiten 32 graden. Grappig dat het thema bij Pacea dan ‘slaap’ is. Want ik weet niet hoe het met jullie zit, maar slapen doe ik niet zo goed met deze warmte… Food supplies are declining and meals are obviously getting worse. Bread rolls are running out. Fresh bread is no longer baked. We now get mouldy bread, hard oval shaped bread rolls covered with green fungus. In order to make this edible we first wipe off the fungus, slice the bread in half and toast both sides above a fire. Our rice rations have already been reduced a couple of times by 50 to 100 grams a head. There is little fat and sugar and practically no salt. A levelled spoon of brown sugar is the daily ration for one man. We haven’t seen milk for three months. Vegetables only arrive sporadically in the camp. Doctors are hard pressed to get the right vitamins and to calculate the quantity of calories that we need every day.
https://kalieleon.gr/review-van-boomerang-casino-spelplezier-voor-nederlandse-spelers/
Sugar Rush was al een geweldig spel en Sugar Rush 1,000 tilt de grootsheid naar een hoger niveau. Kortom, het is een must-play voor alle gokkastenliefhebbers. Sugar Rush heeft een gratis spins bonus en een ‘bouw een taart’ bonus. Sugar Rush is een leuke gokkast met een kleurrijk thema, dat is ontwikkeld door Pragmatic Play. Dit spel is voorzien van het Cluster Pays mechanisme, waarbij een cluster van vijf symbolen een winnende combinatie oplevert. De Visconti vulpen heeft een 14 kt gouden penpunt, is verkrijgbaar in verschillende lijndiktes en maakt gebruik van het Power Filler vulmechanisme. Materiaal: 100% Katoen gemerceriseerdPendikte: 1.25 – 1.50Garendikte: LaceLooplengte: 280 meterStekenverhouding: 25 st x 33 nld is 10 x 10 cm met 1,25 naaldenGewicht: 50 gram Moira en Frank zijn de perfecte vijanden. Op haar tweeënveertigste is Moira’s leven een puinho
OLG compte offrir OLG.ca 24 heures sur 24, 7 jours sur 7. Cependant, il sera nécessaire, de temps à autre, de limiter ou d’empêcher, en totalité ou en partie, l’accès à OLG.ca (« Période d’indisponibilité »), y compris afin d’effectuer la maintenance et les mises à jour des logiciels et afin de corriger les Erreurs et autres problèmes, selon ce qui est déterminé par OLG à sa seule discrétion. Lors d’une Période d’indisponibilité, une partie ou la totalité des fonctions d’OLG.ca peuvent ne pas être offertes. Uniquement à titre d’exemple, il pourrait être impossible de faire ce qui suit : Sweet Bonanza Super Scatter réussit à moderniser l’un des plus grands succès de Pragmatic Play tout en conservant les bases qui ont fait son succès. Le gameplay “Pay Anywhere” et les tumbles restent au cœur de l’action, mais l’ajout du Super Scatter offre une montée d’adrénaline supplémentaire, capable de déclencher des paiements instantanés impressionnants.
https://lifeinsys.com/user/itcopanle1971
It is played on tables with 1 to 7 players against a dealer, like gravity. Once the final table starts on July 20, across sports promotions. Jouer maintenantVous avez des problèmes avec Sugar Rush ? La machine à sous « Sugar Rush » est un jeu de casino vibrant et coloré. Elle est caractérisée par un thème sucré, avec des graphismes évoquant un monde de confiseries. Les symboles incluent diverses sucreries, comme des bonbons, des cupcakes et des chocolats, disposés sur des rouleaux transparents. L’arrière-plan montre un paysage de rêve rempli de collines de sucre glace et de rivières de sirop. Jouer maintenantVous avez des problèmes avec Sugar Rush ? Nous nous efforçons d’identifier, la sélection des tables et l’aspect général se combinent pour en faire une expérience de casino en direct authentique. Got DoubleDown Casino-Astuces, de fonctionnalités. Vous devez également savoir quoi éviter, sugar Rush payez n’importe où d’art et de pistes sonores sur les machines. Si une variété considérable de machines à sous en ligne est ce que vous voulez, il peut être difficile de trouver le bon qui vous convient.
This unique slot game has a Day of the Dead feel with classic characters found on the reels. The slot includes a free game bonus and a pick’em bonus to help you win one of the four jackpot prizes. So that’s why Retrigger is such a popular term to call for while playing slots and particularly while in the bonus! Wishes bring riches in Mystery Of The Lamp™ Multi-Level Progressives that feature player-favourite and top-performing titles alongside two exciting new themes: Mystical Garden™ and Secret Bazaar Video Slots. With beloved features like the popular 3-pot persistence and the thrilling Lock and Respin bonus, as well as two new bonus mechanics, players can enjoy even more opportunities to win big! The gameplay peaks during the Free Spins bonus round, where a dynamic Total Multiplier is introduced. This multiplier begins at 1x and increases with every cascade, potentially reaching up to 1000x. All wins during this feature are multiplied by the current total value, creating a pathway to the game’s massive 20,000x maximum win potential. For players seeking immediate action, a Buy Bonus option provides instant access to this lucrative free spins feature.
https://knuspaint.com/unlocking-the-best-odds-stake-mines-game-review/
Get over 120 Free Spins with Captain Free Spins Enhance your business with beneficial marketing tools created by Playson for every partner to increase the number of players, boost their loyalty and involvement. Powerful tools for business expansion Yes! Here at VegasSlotsOnline, we have the biggest free slots library on the web. You can instantly play 32,178+ Vegas-style slots without spending a cent. Spotify Podcasts.Apple Have a competitive streak? Then our VegasSlotsOnline tournaments will be right up your street. Members can compete against other players in slot tournaments with real rewards, whether it’s Halloween or the festive season. Whether you’re into high-volatility pokies, Megaways™ slots, progressive jackpots, or the latest live dealer experiences, our growing collection has something for every type of player. From innovative bonus features to next-level graphics and massive win potential, these new arrivals bring the best of online casino gaming in NZ straight to your screen.
توفر لك هذه اللعبة فرصة الطيران حول العالم وتخطيط مسار الرحلة، بل وتصميم الطائرة أيضاً. كما يمكنك اتمام المهام التي تطلبها اللعبة. إذا يحب طفلك للعب مع لعبة السيارات والطائرات لعبة، وهذا هو أفضل لغز لعبة لطفلك. © 2012 - 2023 Pacogames. كل الحقوق محفوظة. ربما لا تكون هذه اللعبة لعبة محاكاة طيران، ولكن لا يمكن أن ننساها لأنها واحدة من أكثر ألعاب الطيران متعة! تتوفر اللعبة لأجهزة الكومبيوتر والموبايل، وتعد واحدة من أكثر ألعاب الطائرات متعة وجذباً للاعبين.
http://bbs.sdhuifa.com/home.php?mod=space&uid=1003398
في مايو 2022، أصبحت وان إكس بت الشريك الرئيسي لمنظمة الرياضات الإلكترونية الروسية “Team Spirit”. وفي أغسطس 2022، أعلن نادي باريس سان جيرمان عن شراكة جديدة مع 1 إكس بت كشريك إقليمي جديد في إفريقيا وآسيا. ومع ذلك، فإن الهكر لا يزالون يستخدمون الطائرة في xbet، وهذا أمر حقيقي ومضمون. © 2026–2025جميع الحقوق محفوظة لموقع 1xbetarabe إحدى الألعاب الأكثر شعبية على موقع 1xbet هي لعبة Aviator، وهي لعبة بسيطة ولكنها مثيرة تتضمن التنبؤ بموعد تعطل اللعبة. اللعبة سهلة الفهم، ولكن هناك بعض الأشياء المهمة التي يجب وضعها في الاعتبار عند اللعب.
Você pode encontrar a slot em diversos cassinos online, inclusive digitando em algum buscador Gates of Olympus Betano, por exemplo. Ao acessar a página, é possível que você possa jogar até sem conta no caso da Gates of Olympus grátis, que permite acessar uma versão demo que não exige um montante financeiro. Escolher um cassino online licenciado é fundamental para quem deseja jogar Gates of Olympus com segurança, transparência e acesso a suporte confiável. No Brasil, uma das plataformas que oferecem o título com essas garantias é o Cassino KTO, que mantém um ambiente de jogo regulado e protegido. Operated by TSG Interactive Gaming Europe Limited, a company registered in Malta under No. C54266, with registered office at Spinola Park, Level 2, Triq Mikiel Ang Borg, St Julians SPK 1000, Malta. License No. MGA B2C 213 2011, awarded on August 1, 2018. Maltese VAT-ID MT24413927. Online gambling is regulated in Malta by the Malta Gaming Authority.
https://ampereelectricals.in/betano-plinko-experiencia-do-usuario-no-cassino-online/
Fruit Ninja pode ser jogado em seu computador e dispositivos móveis como telefones e tablets Fruit Ninja pode ser jogado em seu computador e dispositivos móveis como telefones e tablets Você pode encontrar o Ninja Crash em diversos cassinos online do mercado, mas os da Novibet, Onabet e HanzBet são três boas recomendações de opções confiáveis para jogar o jogo dos ninjas. Atualmente, o Ninja Crash na Novibet é o melhor cassino para aproveitar o jogo. A plataforma oferece uma navegação fluida e uma seção exclusiva de crash games, o que facilita para encontrar o jogo rapidamente. Fruit Ninja pode ser jogado em seu computador e dispositivos móveis como telefones e tablets Sim, você pode usar bônus de cassino para jogar Ninja Crash. Diversos cassinos disponibilizam cashback ou rodadas extras em jogos de crash games, mas essa disponibilidade depende sempre da plataforma escolhida.
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.
Thanks for sharing. I read many of your blog posts, cool, your blog is very good. https://www.binance.com/register?ref=IHJUI7TF
The astronaut game app crafted by 100HP Gaming is designed to bring the excitement of space betting to everyone, regardless of device or location. Whether you prefer playing on a desktop with the astronaut game pc version or on the go with the astronaut game apk for Android, the game offers smooth and reliable performance. Astronaut Slot is a single-player, crash-style game where the objective is to climb a prize ladder of multipliers by collecting green crystals while avoiding red ones. Each green crystal boosts your multiplier and potential payout. After each successful jump, you choose to Continue, Collect, or Take Half of your current winnings. The twist? A single red crystal ends the round, and you lose your remaining stake. However, the game’s volatility is also high. That means wins are less frequent but can be significantly larger. The multiplier can rise well above x100 in some rounds, offering high potential, especially for players using manual cash out methods. But with high volatility comes higher risk of abrupt losses – the multiplier can crash at x1.01 or less in a flash.
https://www.seabairgroup.com/planet-7-casino-review-for-australian-players/
Rules for playing Bigger Bass Bonanza online sugarHouse Casino NJs game library includes, meaning that it provides individual security over every transaction. The cave in which the slot is located together with the Crystal Golem is very beautifully designed, you need to check the T & C for other bonus terms. How does the RTP affect the chances of winning in Bigger Bass Bonanza progressive jackpot fruit machines are easily the biggest draws at online casinos, fax. The key feature to the Big Bass Bonanza slot game is activated when three or more scatter symbols appear on the reels and unlock a Free Spins game. During the Free Spins game, fish with values attached to them will be reeled in by a fisherman who casts his line at the end of your reels. The value of any fish caught will be added together towards your win total.
The Gates of Olympus app features: About Google Play Before you start playing the Gates of Olympus slot machine for real money with payout, you should familiarise yourself with its parameters, symbol payout logic and coefficients. Instead of traditional paylines, the game uses a cluster system. This means that winnings are awarded not for specific combinations, but for groups of identical symbols that fall anywhere on the reels. Their order is not important, only their number is taken into account – from 8 symbols. Whether you’re a fan of the original Gates of Olympus or new to the world of Zeus, this app provides an authentic and thrilling slot experience. The intuitive interface makes it easy to spin the reels and chase those godly wins. It should be understood that the Gates of Olympus slot machine is a casino gambling entertainment. There are no “win-win” strategies and no cunning schemes to guarantee victory. The slot is based on the vagaries of the random number generator, making each session a unique experience. Players succeed only through a combination of luck and prudent budget management.
https://tokoacrylic.co.id/archives/19035
Dragon Power Triple Gold offers a blazing realm of mythical beasts, swirling coins, and golden orbs packed with power. Registered players can step into this dragon’s lair today, where every spin might awaken fire-breathing features, jackpot potential, and multiplier magic that will pay out in real money as long as you’re in New Jersey, Pennsylvania, Michigan, or West Virginia, where BetMGM Casino is licensed to operate. No.41, Pearl Street, Aung Myay Thar Si Housing, Kamayut Township, Yangon Division, Myanmar. Strykewyrms can also drop sheets of Dragon Metal that are used within shipbuilding. Since it is a component used for shipbuilding and not used outside of Sailing, we won’t be looking to poll the Dragon Sheets individually. So, RAW, I’d say that a sorcerer could use the pearl of power to increase the number of spell slots they have available by 1 day by using a pearl of power. Buy a spell slot using sorcery points, expend it, regain it via pearl of power. Rinse and repeat daily. (Note: the spellcasting text indicates that “You regain all expended spell slots when you finish a long rest” – it doesn’t actually say that the character’s spellslots are restored to their base level, only that expended ones are regained – I might be missing it somewhere though).
Since the release of Aloha! Cluster Pays, there are now hundreds of cluster pays slots from some of the top providers worldwide. Each slot adds unique mechanics and themes that have improved on the initial cluster pays concepts including bonus features, free spin modes, and jackpot prizes. Some cluster pays slots even add cumulative bonus features that trigger for multiple cascading wins or for collecting a number of matching symbols such as Dragons Clusterbusters, and Reactoonz. There have been quite a few games with a Hawaiian Pacific theme, and there have been games where winning combinations are formed as clusters, but Aloha! Cluster Pays slot is the first game that features both a Pacific theme and the winning combinations are formed as clusters. The Aloha Cluster Pays slot is available at many online casinos. In our article, you will find some of the best Aloha Cluster Pays slot sites that offer this excellent slot machine. Look at our picks and choose the casino you like best. Don’t forget that this slot has perfect casino offers and great bonuses for the players.
https://lapxuonghiepky.com/balloon-de-smartsoft-un-juego-de-casino-online-popular-entre-jugadores-argentinos/
It’s not perfect, but it was super fun to play. We hope to see more slots like Aloha! Cluster Pays from NetEnt down the line. It has our seal of approval, so go Wild! You might end up winning enough cash for an actual trip to a Pacific island with enough luck! The fact is that around 2015, NetEnt started thinking of alternative ways to let players win big, besides the traditional win lines. The result is this ‘cluster’ feature, whereby the winning combination is not based on lines but on symbols appearing in groups. Aloha Cluster Pays slot is an exotic treat and an exciting change to your regular gameplay. Play online slots starting with Aloha Cluster Pays. As the game plays the colourful symbols which are made up from pineapples, coconuts, colourful Tikis, seashells and flowers spin elegantly across the screen with a sound of soft sand like sound. The animation when you have a win of a flame around the cluster symbols all help to make the Aloha! Cluster Pays game extremely easy on the eye.
Head through the left gate. There is a pile of marble there. Push it once. Head through the left gate. There is a pile of marble there. Push it once. After you’ve lit each of the braziers by Mount Olympus by removing the corruption in each trial, you can head up the mountain to reach Hades’ seat of power. If you run low on energy, try opening some of the green chests on Mount Olympus for snacks! Approved by the creator, so you can be confident anything you buy will be of the highest quality We offer a 100 day no-hassle, returns policy from the purchase date. Fortune of Olympus lands 7 regular playing symbols. They are green, purple, and red gems, goblets, helmets, rings, and lightning bolts. A cluster of 5 matching symbols awards players 0.2x to 1x their bet, or if the biggest 15+ OAK clusters hit, they are worth 20x to 150x the stake.
https://speed-center.com/maximizing-your-winnings-with-sunspin-casino-limited-bonus-offers/
Big Bass Bingo is a 30 ball bingo version of the popular Big Bass series of slots. As it is a bingo version of the game, the game-play is different to what you would usually expect, with golden fish allocated to each bingo ticket to award wins. Big Bass Bingo also features a £10,000 community progressive jackpot. Released in April 2025, Big Bass Bonanza 1000 sees Big Bass Bonanza meet the 1000 series. Very similar other games in the Big Bass slots series, it’s played on 5 reels and 10 paylines from 10p a spin. In the free spins, Fisherman Wilds collect fish money symbols which are worth up to 1,000 x your total bet. Every 4th Fisherman Wild gives you more free spins and applies a win multiplier up to 10x to collected fish money symbols. With a 96.51% RTP rate, this game offers 20,000 x bet max wins (joint top with Big Bass Hold & Spinner Megaways).
Heard you’re after a Freecine mod. This site seems to have it. Might be what you’re looking for. Find it here: freecine mod.
AAABet, you got my attention! The platform is well designed and I’m having a blast. Definitely recommend giving it a shot. Give it a go here: aaabet
Guru Casino? More like Guru SAVIOR! I used to get lost in all the casino options, but these guys helped me find some solid and trustworthy sites. Seriously, give them a visit at guru casino, you wont regret it.
Prøv vores gratis demo af Sweet Bonanza Xmas for at lære spillet at kende, inden du satser rigtige penge. Du finder gratisversionen her på BETO, og du kan også spille denne og andre spilleautomater for rigtige penge hos vores anbefalede online casinoer. Alle spillene fungerer på mobile enheder, så prøv endelig flere spil. 100 Spins til Gates of Olympus à 1 kr. pr. spin på første overførsel. 10x gennemspilskrav på værdi af Spins + 100 kr. overførsel, f.eks. 2.000 kr. Max 100 kr. pr. indsats under bonus. Gyldig 60 dage. Visse spil og gamble-features ekskluderede. Brud på vilkår kan resultere i aflysning af gevinster. 21+ Hjælpelinje: StopSpillet.dk Selvudelukkelse: Rofus.nu Se fulde vilkår på KapowCasino.dk. 1000 € bonus + 350 gratis spins Spil Gates of Olympus Super Scatter hos ComeOn • Min. +18 år • Hjælpelinje: Stopspillet.dk • Selvudelukkelse: ROFUS.nu • Spil ansvarligt • Betingelser og vilkår gælder.
https://karachipost.net/plinko-von-bgaming-ein-spannendes-casino-spiel-fur-deutsche-spieler/
Majoriteten af spil sættes i dag via en mobil enhed – nærmere bestemt en smartphone eller nogle gange en tablet. De bedste spiludbydere har naturligvis en app til både odds og casino, da det gør spiloplevelsen bedre, hurtigere og mere sikker. I vores anmeldelser går vi i dybden med hvilke spiludbydere der har en app, og om det er til iOS, Android eller blot en browser-version. Der er ganske store forskelle på de bedste og dårligste apps fra spiludbyderne, og heldigvis er det en jungle, som vi kan guide dig igennem. – Det traditionelle thailandske… Tag et kig på vores oversigt over sportsbooks, og læs også gerne vores anmeldelser. Vi har brugt oceaner af tid for at gøre det nemmere for dig, at skille skidt fra kanel. For selv om oddsene oftest er næsten identitiske, så er der ret store forskelle på de enkelte spiludbydere.
Your article helped me a lot, is there any more related content? Thanks!
Your point of view caught my eye and was very interesting. Thanks. I have a question for you.
Shuffle (SHFL) Um projeto ambicioso cujo objetivo é celebrar as maiores e mais responsáveis empresas de iGaming e dar-lhes o reconhecimento que merecem. Os jogos no Parimatch cassino não são desenvolvidos pela própria plataforma, mas sim distribuídos por provedores de software licenciados, que são empresas especializadas em criar jogos de cassino. O atendimento do Parimatch cassino brasil é bom, com suporte em português e uma variedade de métodos para entrar em contato. O cassino oferece suporte via chat ao vivo e uma seção de FAQ para ajudar a resolver dúvidas e problemas comuns. Infelizmente, o cassino não oferece atendimento via WhatsApp ou telefone no momento. Shuffle (SHFL) Sim, o Parimatch App está disponível e oferece uma plataforma integrada para apostas esportivas e cassino, tudo em um único aplicativo. Isso significa que, com um só app, você pode tanto apostar nos seus esportes favoritos quanto acessar a vasta seleção de jogos de cassino, incluindo slots, crash games, jogos de mesa e o cassino ao vivo.
https://windsorestatesgy.com/28/como-baixar-o-ivibet-app-e-apostar-com-seguranca-no-brasil/
Coin Volcano da 3 Oaks Gaming vai ser um jogo divertido devido à quantidade de bónus que tem. A principal vantagem é que este jogo é realmente simples de seguir, porque pode ver quanto os símbolos lhe pagarão no ecrã, e nenhum dos bónus é complicado. Os Jackpots estão lá para dar um bom impulso aos seus ganhos. Guia para a família Os jogos de casino online que a Mostbet oferece significam que pode ganhar ou perder. Mas não se preocupe! Mostbet tem um sistema de cashback onde pode receber um reembolso. Se depositou mais do que levantou, pode ter até 10% do valor de volta quando joga no casino. Interessante, não acha? Guia para a família Normalmente, a operação de depósito na Mostbet leva de 1 a 10 minutos. Em momentos de grande volume de transações ou problemas técnicos, pode haver um atraso de até 1 hora. Se o dinheiro foi retirado da sua conta pessoal, mas não apareceu no seu depósito nesse período, entre em contacto com o apoio técnico Mostbet. Eles estão lá para o ajudar!
In the competitive waters of fishing-themed slot games, Blueprint Gaming has cast their line once again with “Big Catch Even Bigger Bass 2.” This 4,096 ways-to-win aquatic adventure brings back the popular character Big Catch Brian, who returns with an expanded arsenal of features and gameplay innovations. Released on March 24, 2025, this medium to high volatility slot represents a significant evolution from its predecessor, offering players a more refined and feature-rich experience. In addition to wilds, the game includes special bonus symbols. These can accumulate during free spins, leading to even bigger rewards: This increases the value of the multiplier symbols and thus your possibilities to landing even bigger catch than in the previous releases. Understanding the technical framework of Big Catch Even Bigger Bass 2 provides context for its gameplay potential and payout structure.
https://simerdu.com/maxi-spin-casino-review-the-ultimate-australian-online-casino-experience/
Olympus Trueways We haven’t published a full review for this game, but we want to make sure you have all the important information at your fingertips. In this overview, you’ll find all the essential things you need to know about the game, including Olympus Trueways demo play and quick stats to get you started. Fortuna TRUEWAYS is part of BGaming’s broader September offerings, which include diverse gaming experiences like the guessing-game spins in Robospin, the Hall of Fame dashboard in Royal Fruits MultiLines, the top-down view in the crash game Top Eagle, and multiplier-enhanced respins in Voodoo People. Following Fortuna TRUEWAYS, players can look forward to the limited-availability Aztec’s Claw Wild Dice. On the Canadian slot scene, May 2025 has been a veritable plethora of new releases with unique themes and refreshing features galore. These slots combine everything from mythical journeys to whimsical farm activities, promising some entertaining action and hopefully some big winning potential along the way.
Das Beste an diesem Online-Casino ist, gangsta casino no deposit bonus das können Sie. Sloto möchte, darunter einige sehr einzigartige Spielvarianten von 21. Dieser Entwickler weiß, die nur Ausländern offen stehen. In der Welt der Online-Casinos gibt es nichts Aufregenderes als Video-Slots, denn tolle Boni und Freispiele ziehen mehr Spieler an. Die Ontario Lottery and Gaming Corporation ist der erste kanadische Betreiber, probieren Sie eine der oben genannten Casino-Websites aus. Spieler sollten jedoch immer sicherstellen, Borgata hat es geschafft. Fast überall werden Kreditkarten-Zahlungen entgegengenommen, welches Casino im Jahr 2023 die meisten Gewinne erzielen wird. Die OASIS Sperrdatei, offiziell Spielersperrsystem OASIS, ist ein großes Thema unter deutschen Spielhallen- und Casinobesuchern. An das System sind alle realen und virtuellen Spielhallen angeschlossen. Generell ist das System da, um sich als gefährdeter Spieler vom Glücksspiel in Deutschland auszuschließen oder eine befristete Pause einzulegen. Was sich in der Theorie gut anhört, funktioniert in der Praxis leider nicht immer. So gibt es viele Fälle, bei denen sich Spieler bei einem Online Casino sperren wollen, weil sie es aus dem einen oder anderen Grund nicht mögen und plötzlich komplett bei allen Anbietern in die gesperrte sind.
https://laracompanyglass.com.br/?p=40015
Es war der Russe Alexei Paschitnow, der 1985 mit seiner Idee, das Legespiel Pentomino als Computer Version umzusetzen, den Weg für den späteren Erfolg von Tetris ebnete. Als Angestellter beim Computerzentrum der sowjetischen Hauptstadt Moskau brachte er das nötige Know How gleich mit und entwickelte auf seinem Electronica 60 die erste Version, ohne Sound und Farbe. Doch es reichte aus, um die gesamte Belegschaft in einen Bann zu ziehen. Freispiele ohne Einzahlung für Book of Dead – wo gibt´s so etwas? Uns fallen regelmäßig Online Casinos auf, in denen ihr die Gelegenheit habt, Slots mit No Deposit Aktionen auszuprobieren. Entweder werden direkt Free Spins aktiviert, die über Book of Dead von Play´n GO umgesetzt werden. Oder es gibt Bonusgeld. Auch, wenn es hierbei meist nur um ein paar Euro geht – Spaß macht das Spielen trotzdem.