Cryptographic failures remain one of the most critical risks in modern security systems. In fact, the exact focus keyword cryptographic failures appears as the second item in the OWASP Top 10—highlighting how common and devastating these weaknesses can be.
In this detailed guide, we will explore why cryptographic failures happen, how they are exploited in real-world attacks, and 7 powerful, actionable ways to prevent them in your systems. Whether you’re a cybersecurity beginner or a seasoned engineer, this guide will help you harden your applications against modern cryptographic threats.
What Are Cryptographic Failures?
Cryptographic failures refer to security vulnerabilities that arise when sensitive data is not properly encrypted, is encrypted using weak methods, or is exposed due to poor implementation practices. These failures occur in multiple layers of an application—transport, storage, authentication, and API communication.
Common LSI/semantic terms used naturally:
- broken cryptography
- weak encryption
- insecure hash functions
- insecure transport layer
- plaintext exposure
- encryption misconfigurations
In a world where everything—from login passwords to API tokens—relies on encryption, cryptographic failures act like opening the doors for attackers.
Why Cryptographic Failures Still Happen
Despite decades of research, cryptographic failures remain widespread due to:
- Developers misusing crypto libraries
- Legacy systems relying on outdated algorithms
- Hardcoded keys stored in source code
- Applications transmitting data without TLS
- Misconfiguring certificate validation
- Using weak or deprecated hash functions like MD5 or SHA1
Even large companies continue to face severe data breaches simply because of poor cryptographic hygiene.
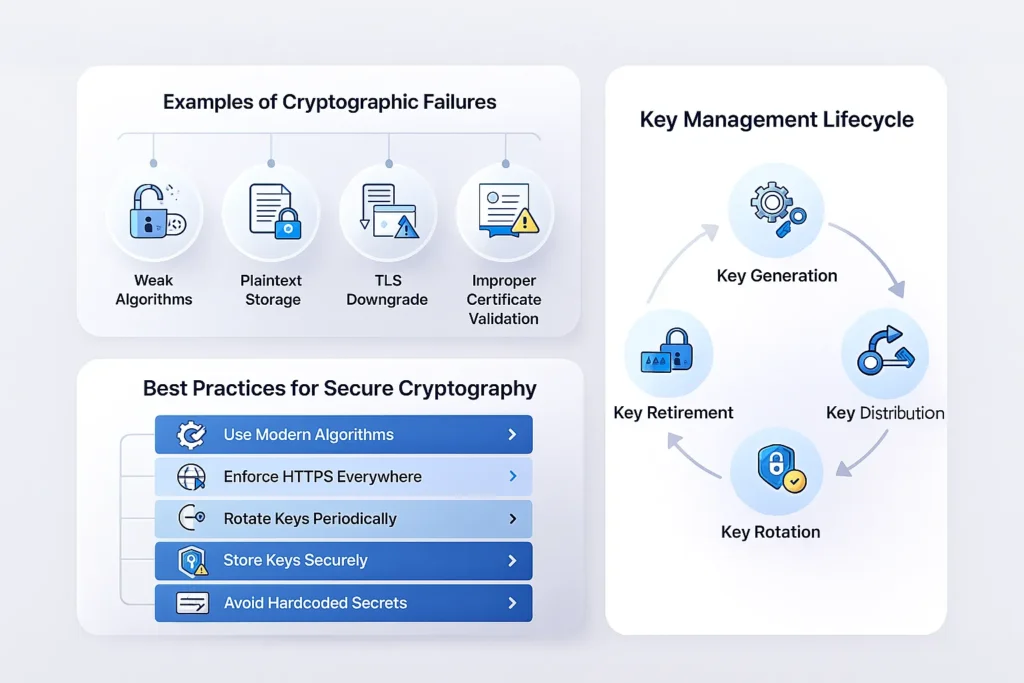
Real-World Examples of Cryptographic Failures
1. Heartbleed (2014)
The Heartbleed bug in OpenSSL allowed attackers to read memory directly from secure servers. Although not a direct algorithm failure, it demonstrated how improper crypto implementation can collapse entire security models.
2. WhatsApp Pegasus Exploit
An unpatched cryptographic flaw in WhatsApp allowed attackers to execute code using malformed packets—even without user interaction.
3. Storing Passwords in Plaintext
Multiple large companies (LinkedIn, Adobe, Canva) have been breached after storing passwords using weak hashing techniques.
4. TLS Downgrade Attacks
Attackers force the connection to downgrade from TLS 1.3 → TLS 1.0 to exploit known weaknesses.
7 Powerful Ways to Prevent Cryptographic Failures
1. Use Strong, Modern Cryptographic Algorithms
Weak or deprecated algorithms such as MD5, SHA1, RC4, DES, or 3DES must be eliminated.
Recommended algorithms/protocols:
- AES-256-GCM for encryption
- SHA-256 / SHA-3 for hashing
- RSA-2048 or ECDSA P-256 for signing
- TLS 1.3 for secure communication
If you use outdated crypto, your security collapses instantly.
2. Enforce HTTPS Everywhere
Always ensure:
- No HTTP fallback
- HSTS enabled
- TLS 1.2+ minimum
- Proper cipher suites
A simplified Nginx TLS 1.3 configuration:
ssl_protocols TLSv1.3;
ssl_prefer_server_ciphers on;
ssl_ciphers 'TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256';
3. Never Roll Your Own Crypto
Custom-built cryptographic functions are the fastest way to get hacked.
Use trusted libraries:
- OpenSSL
- libsodium
- BoringSSL
- wolfSSL
Never attempt to build your own hashing, key generation, or encryption logic.
4. Implement Proper Key Rotation
Long-lived keys increase risk.
You should:
- Rotate encryption keys periodically
- Use Key Management Services (AWS KMS, HashiCorp Vault)
- Enforce key expiry policies
5. Secure Storage and Transit of Keys
Store keys in:
- HSMs
- KMS
- Vault systems
NEVER store keys in:
- GitHub repositories
- Docker images
- WordPress settings
- Environment variables without encryption
6. Avoid Hardcoded Secrets
Attackers scan codebases for secrets.
Use:
aws secretsmanager get-secret-value ...
Or HashiCorp Vault dynamic secrets.
7. Validate Certificates Correctly
Incorrect certificate validation allows MITM attacks.
Ensure:
- Hostname validation
- Certificate expiry checks
- Pinning where possible
- Avoid disabling certificate checks in development
Cryptographic Failures Detection Strategies
Security teams should:
- Perform TLS scans
- Integrate SAST tools (Semgrep, SonarQube)
- Run dependency scans
- Validate certificates with SSL Labs
- Monitor for plaintext logs and leaked secrets
OWASP Cryptographic Failures Guide:
https://owasp.org/Top10/A02_2021-Cryptographic_Failures/
People Also Ask
1. What causes cryptographic failures?
Poor implementation, outdated algorithms, weak TLS settings, and insecure key management.
2. Which algorithms should I avoid?
MD5, SHA1, RC4, DES, 3DES.
3. How do cryptographic failures impact security?
They lead to stolen passwords, MITM attacks, data breaches, and impersonation.












Checking out 11uubet. Their site looks pretty clean, a little modern. Games seem standard, but they’ve got some decent promo offers. Worth a peek, perhaps? Give it a go: 11uubet
Understanding the risks of cryptographic failures is so important, especially given how frequently they occur as mentioned in the article. I also found some related discussion on https://tinyfun.io/game/stupidella-horror-2 that offered a different perspective on potential vulnerabilities.
7359betplataforma, nice platform, all the games I want are right here. Give it a look. Explore the platform at 7359betplataforma.
VN88ME, shoutout! Quick signup, smooth gameplay and the support team isn’t a bunch of bots. That’s a win in my book. Go peep it: vn88me
Your article helped me a lot, is there any more related content? Thanks!
25bet9, eh? Haven’t heard of them before, but… Worth checking out at least once. See what they offer here:25bet9
Popped into AF88GAME. The loading times were quick, which is a massive plus in my book. Nothing worse than waiting forever, right? Gameplay was smooth too. Worth a look! Find out more: af88game
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article. https://www.binance.com/register?ref=IHJUI7TF