OWASP Authentication Failures remain the leading cause of breaches across web apps, mobile apps, APIs, cloud systems, and microservices. This extended edition (3000+ words) covers every angle: deep technical analysis, attack chains, red-team techniques, real-world breaches, mitigations, cloud pitfalls, SOC detection rules, and a complete operational playbook.
Table of Contents
- Introduction
- Why Authentication Fails
- 7 Authentication Failures — Deep Technical Breakdown
- Cloud & DevOps Authentication Pitfalls
- Mobile Authentication Weaknesses
- Real-World Breaches & Postmortems
- Advanced Mitigations & Playbook
- Detection & Monitoring for SOC Teams
- FAQ + Schema
Introduction
This extended guide is designed for cybersecurity engineers, developers, penetration testers, red teams, SOC analysts, and cloud architects. It goes beyond the OWASP Top 10 definition of Authentication Failures and explores how attacks occur in real modern infrastructures.
Why Authentication Fails — The Real Root Causes
- Protocol complexity: OIDC, OAuth 2.1, JWT, SAML, WebAuthn introduce many misconfigurable components.
- Human error: Password reuse, phishing, social engineering remain large factors.
- Developer shortcuts: DIY crypto, poor session regen, trusting defaults.
- Operational oversights: leaked secrets in CI/CD, exposed backups, overly permissive IAM roles.
- Lack of Zero Trust mindset: identity is not continuously verified across sessions.
The 7 Powerful OWASP Authentication Failures (Extended Breakdown)
1. Weak Password Policies
Weak passwords remain extremely common, even in enterprises. Attackers exploit password spraying and credential stuffing to compromise thousands of accounts with minimal effort.
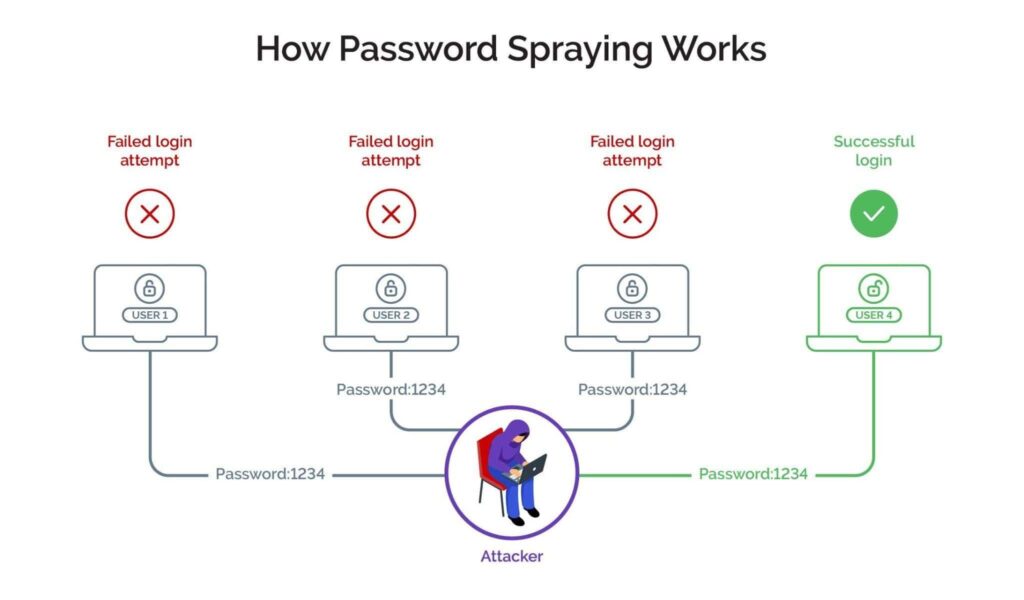
Technical Indicators
- Password length under 10 characters
- No breach-password comparison using APIs
- Password = username or predictable pattern
- No rate limiting or IP throttling
Remediation
- 14+ character passphrases (NIST 800-63B)
- Block known breached passwords
- Educate users about password reuse danger
- Implement adaptive rate limiting + CAPTCHA
2. Credential Stuffing & Brute Force Attacks
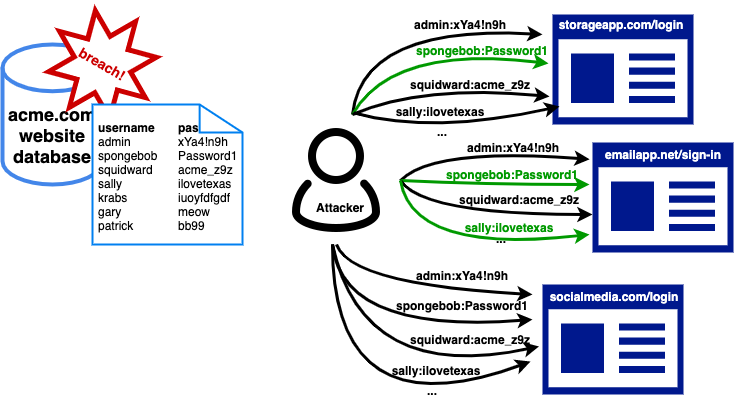
Credential stuffing leverages large leaked databases. Attackers use distributed botnets, rotating proxies, and CAPTCHA-solving APIs.
Secure Rate Limiting Example (Express + Redis)
const rateLimit = require('express-rate-limit');
const RedisStore = require('rate-limit-redis');
const limiter = rateLimit({
store: new RedisStore({ client: redisClient }),
windowMs: 60 * 1000,
max: 5,
message: 'Too many attempts.'
});
app.post('/login', limiter, loginHandler);Mitigation
- Device/browser fingerprinting
- Behavioral anomaly detection
- Bot management platforms (Cloudflare, Akamai)
- Global throttling across username and IP
3. Session Hijacking & Fixation
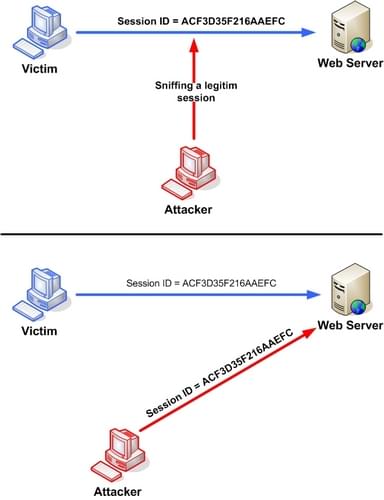
Attackers steal or replay session tokens. This includes cookie theft, XSS-driven hijacking, token replay attacks, and session fixation (attacker pre-seeds a session ID).
Secure Cookie Example
Set-Cookie: session=XYZ; HttpOnly; Secure; SameSite=Strict; Path=/; Max-Age=1800Mitigation
- Always regenerate session ID on login
- Use HttpOnly + Secure + SameSite cookies
- Short-lived JWT access tokens
- Refresh token rotation with reuse detection
4. Missing or Weak MFA
MFA blocks 99% of credential-based attacks, but only when implemented using secure forms.
- Best MFA: WebAuthn (FIDO2 hardware keys)
- TOTP apps are strong but still phishable
- SMS OTP is weak (SIM swap, SS7 attacks)
- MFA fatigue attacks target push-based MFA
5. Insecure Credential Storage
Weak hashing (MD5, SHA1), plaintext password storage, or poor key rotation can destroy security instantly.
// Secure Argon2 hash example
const argon2 = require('argon2');
const hash = await argon2.hash(password, { type: argon2.argon2id });- Encrypt database backups
- Rotate KMS keys every 90 days
- Scan repositories for secret leakage
6. Logic Flaws in Authentication Flows
These flaws do not require cracking crypto—they exploit mistakes in the login/reset flow design.
- Password reset without identity verification
- Magic links without expiration
- SSO flows that auto-create accounts improperly
// Secure reset token
const crypto = require('crypto');
const token = crypto.randomBytes(32).toString('hex');7. Misconfigured Identity Providers (OAuth / OIDC / SAML)
- Accepting unsigned JWTs (“alg: none”)
- Missing issuer (iss) and audience (aud) validation
- Wildcard redirect URIs
- No scope minimization
Cloud & DevOps Authentication Pitfalls
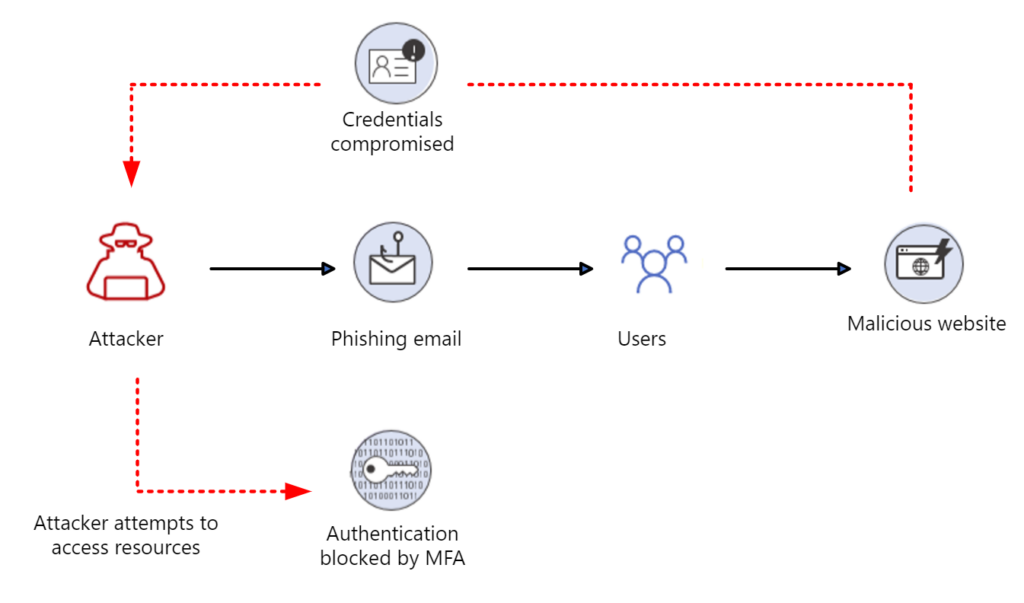
- AWS IAM users with static keys + no MFA
- Kubernetes service account token exposure
- Secrets logged in CI/CD pipelines
Mobile Authentication Weaknesses
- Storing tokens in SharedPreferences / NSUserDefaults (plaintext)
- Unsecured deep link login
- Reverse engineering revealing API keys
Real-World Breaches & Postmortems
Colonial Pipeline (2021)
Single VPN account without MFA → ransomware attack → nationwide infrastructure impact.
Uber MFA Fatigue Attack (2022)
Attackers repeatedly spammed MFA push notifications until an employee finally accepted.
Facebook OAuth Token Leak (2018)
Access token exposure allowed account impersonation at scale — highlights token handling risks.
Advanced Mitigations & Operational Playbook
Short-Term Actions (0–30 days)
- Enable MFA everywhere
- Add rate limiting & CAPTCHA
- Rotate all sensitive credentials
Mid-Term (30–90 days)
- Migrate to WebAuthn for admins
- Implement breach-password checks
- Harden password reset flow
Long-Term (90+ days)
- Adopt Zero Trust authentication
- Token binding + short TTLs
- Annual red-team auth testing
Detection & Monitoring for SOC Teams
| Detection | Why it Matters | Alert Level |
|---|---|---|
| Failed login spikes | Credential stuffing | High |
| Refresh token reuse | Token theft | Critical |
| MFA approved from new country | Account takeover | High |












Heard about bj88thailand from a mate who said it was pretty popular. Thinking of checking it out, heard the slots are good. Try it out and see for yourself: bj88thailand
Alright, lads, just gave 54bets a whirl. Not bad, not bad at all! Pretty straightforward site to navigate and had a good selection of games. Worth a punt! Check ’em out: 54bets
Downloaded the 29betapp recently and it’s pretty smooth. Easy to navigate, and I haven’t had any glitches so far. Definitely beats using the website on my phone all the time. Check it out here: 29betapp