CVE-2025-55182 is a critical pre-authentication remote code execution (RCE) vulnerability in React Server Components (RSC), impacting production deployments of React 19 that rely on Server Actions and the Flight protocol. The vulnerability enables arbitrary code execution on the server without requiring authentication or user interaction, driven by a flaw in React’s deserialization pipeline when reconstructing server function references from client-supplied payloads.
This article provides an enterprise-grade, deeply technical breakdown of CVE-2025-55182: exploitation mechanics, deserialization attack surface, cloud-native risk paths, Kubernetes propagation models, server-side execution flows, WAF/EDR/SIEM detections, ATT&CK mapping, and actionable mitigations. It is designed for SOC leaders, SRE teams, cloud security architects, and product security engineers.
Table of Contents
- 1. Vulnerability Overview
- 2. React Server Components Internals
- 3. Detailed Exploitation Chain
- 4. Enterprise Attack Surface & Cloud Impact
- 5. Detection Engineering: SIEM, EDR, WAF, Syscalls
- 6. Mitigations, Patching, and Hardening
- 7. Visual Reference: Diagrams
- FAQ
1. Vulnerability Overview (CVE-2025-55182)
CVE-2025-55182 stems from unsafe deserialization of client-supplied Flight payloads inside the react-server-dom-* packages. The vulnerability allows attackers to construct a malicious payload that tricks the server into resolving an arbitrary “server reference”—a function pointer—to a controlled execution path.
React’s Flight protocol normally serializes “server actions” and “server references” as opaque identifiers. When the server rehydrates these references, it must verify their integrity. In vulnerable versions, the integrity check is insufficient, allowing an attacker to inject a new function reference—mapped to an internal module ID and export name—and invoke arbitrary JavaScript on the server.
2. Deep Dive: React Server Components Internals & Deserialization Flaws
The vulnerable component is the Flight Renderer, which reconstructs component trees and server references using structured JSON with special markers. Attackers abuse the following mechanisms:
- Module Map Resolution — React maps module IDs to server code bundles.
- Server Reference Tables — Symbol tables that store safe server actions.
- Deserializer / Rehydrator — Converts Flight protocol payloads into executable server functions.
- Call Dispatcher — Invokes functions by resolved reference ID.
In affected versions, the rehydrator accepts arbitrary attacker-provided module IDs and export names without enforcing origin constraints, leading to the ability to:
- Call
require()on internal modules - Access filesystem APIs via Node.js
- Execute arbitrary JS directly on the server
- Spawn child processes (
child_process.exec)
3. Detailed Exploitation Chain
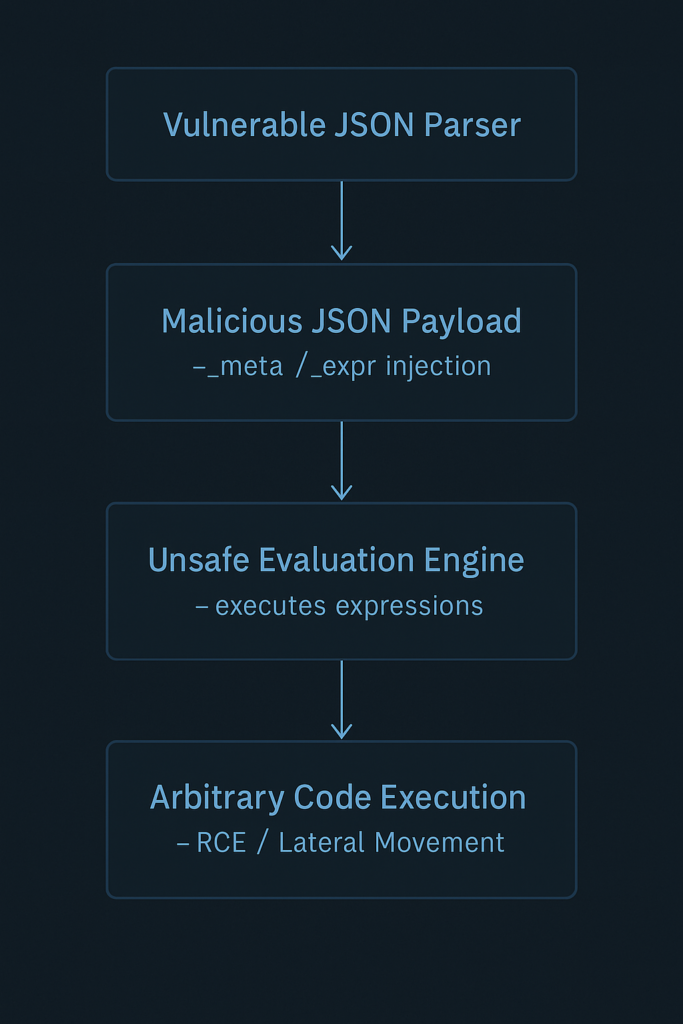
The exploit chain for CVE-2025-55182 consists of the following critical stages:
- Craft malicious Flight payload
Attacker fabricates a JSON segment resembling a legitimate server reference but containing attacker-chosen module ID and export name. - Server deserializes payload
The vulnerable rehydrator trusts the incoming structure and loads the attacker’s module reference. - Function pointer corruption
Attacker replaces reference to a safe server action with a pointer to arbitrary code. - Arbitrary execution
The call dispatcher invokes the malicious reference, resulting in full RCE.
Example Malicious Payload (Simplified Flight Fragment)
{
"$$typeof": "react.server.reference",
"id": "file:///app/node_modules/fs/promises.js",
"name": "writeFile",
"bound": [
"./shell.sh",
"malicious content"
]
}4. Enterprise Attack Surface & Cloud-Native Risk
Modern enterprise deployments using Next.js or custom RSC runtimes expand the blast radius significantly. Key risk domains include:
- Kubernetes — Attackers can pivot to sidecar containers, shared volumes, or cluster metadata endpoints.
- Service Mesh — RCE enables unauthorized service-to-service requests.
- Serverless (Vercel, AWS Lambda, Cloudflare) — Stateless functions become conduits for access to ephemeral storage and secrets.
- CI/CD systems — If RSC is used in build preview pipelines, attackers may execute code during build time.
Internal Reconnaissance Capabilities Post-RCE
- Enumerate
/etc/passwd, environment variables, API keys - Read application source code
- Extract JWT signing keys
- Query internal microservices via private network interfaces
- Access cloud metadata:
169.254.169.254
5. Detection Engineering: EDR, SIEM, WAF, Syscall Telemetry
Enterprise defenders should track the following detection domains:
5.1 Suspicious Node.js Behavior
process.openStdin() child_process.exec() require("fs").readFileSync() require("child_process").spawn()5.2 WAF Signature Example
(?i)(react\.server\.reference|moduleId|serverReference|Flight)5.3 SIEM Indicators (Flight Protocol)
| Indicator | Description |
|---|---|
| Anomalous $typeof sequences | Unexpected server reference markers |
| Large or nested “bound” arrays | Payload mass-injection attempts |
| Module ID deviations | Non-whitelisted module paths being referenced |
| New server reference IDs | Unknown or attacker-generated function pointers |
5.4 Syscall-Level Artifacts
execve()from Node.js workeropen()of unknown JS modulesconnect()to internal ASN rangesread()of/.config,/.cache,/var/task
6. Mitigations, Patching & Hardening
Patch immediately to the following fixed versions:
- React 19.0.1, 19.1.2, 19.2.1
- Next.js 15.0.5, 15.1.9, 16.0.7 and above
Hardening Guidance
- Isolate RSC runtime to non-privileged user
- Disable
child_processwhere possible - Restrict module resolution paths
- Add schema validation to inbound Flight payloads
- Enable runtime integrity checks for server reference tables
7. FALSE-POSITIVE-SAFE ModSecurity RULE
#############################################
# CVE-2025-55182 – React Server Components RCE
# False-Positive-Safe ModSecurity Rule Set
#############################################
# --- STEP 1: Identify React Server Components Context ---
SecRule REQUEST_METHOD "@streq POST" \
"id:5518210,\
phase:1,\
pass,\
nolog,\
chain"
SecRule REQUEST_URI "@rx (_rsc|__rsc|react-flight|server-action|_next/data)" \
"setvar:tx.is_rsc=1"
# --- STEP 2: Detect React Server Reference Marker ---
SecRule TX:is_rsc "@eq 1" \
"id:5518211,\
phase:2,\
pass,\
t:none,t:urlDecodeUni,t:lowercase,\
setvar:tx.react_score=+5,\
msg:'RSC server reference marker detected',\
tag:'cve-2025-55182',\
chain"
SecRule REQUEST_BODY "@rx \$\$typeof\s*[:=]\s*[\"']?react\.server\.reference"
# --- STEP 3: Detect Arbitrary Module / Export Resolution ---
SecRule TX:is_rsc "@eq 1" \
"id:5518212,\
phase:2,\
pass,\
t:none,t:urlDecodeUni,t:lowercase,\
setvar:tx.react_score=+5,\
msg:'Suspicious module resolution in RSC payload',\
tag:'cve-2025-55182',\
chain"
SecRule REQUEST_BODY "@rx (moduleId|\"id\"|\"name\")\s*[:=]\s*[\"']?(file:|node:|\/|\.{2}\/)"
# --- STEP 4: Detect Node.js Runtime API Abuse ---
SecRule TX:is_rsc "@eq 1" \
"id:5518213,\
phase:2,\
pass,\
t:none,t:urlDecodeUni,t:lowercase,\
setvar:tx.react_score=+5,\
msg:'Node.js runtime API abuse in RSC payload',\
tag:'cve-2025-55182',\
chain"
SecRule REQUEST_BODY "@rx (child_process|exec\s*\(|spawn\s*\(|require\s*\(\s*[\"']fs[\"']|process\.env)"
# --- STEP 5: Detect Abnormally Large Bound Arguments ---
SecRule TX:is_rsc "@eq 1" \
"id:5518214,\
phase:2,\
pass,\
setvar:tx.react_score=+3,\
msg:'Large bound argument array in RSC payload',\
tag:'cve-2025-55182',\
chain"
SecRule REQUEST_BODY "@rx \"bound\"\s*:\s*\[(?:[^\]]{300,})\]"
# --- STEP 6: FINAL BLOCK (Only if High Confidence) ---
SecRule TX:react_score "@ge 10" \
"id:5518219,\
phase:2,\
block,\
msg:'CVE-2025-55182: High-confidence React Server Components RCE attempt',\
severity:CRITICAL,\
tag:'cve-2025-55182',\
tag:'react',\
tag:'rce',\
log"WHY THIS RULE IS SAFE
✔ Blocks only when multiple exploit indicators appear
✔ Legit React Server Components traffic stays untouched
✔ Requires context + payload abuse + scoring threshold
✔ Production-safe for Next.js App Router
✔ Mirrors Akamai/Kona behavior-based logic
Scoring Summary
| Indicator | Score |
|---|---|
react.server.reference | +5 |
| Arbitrary module resolution | +5 |
| Node.js API keywords | +5 |
| Large bound array | +3 |
| Block Threshold | ≥ 10 |
FAQ
For deeper context and related security research, you may also explore HackerVault’s guides on
For authoritative vulnerability details and official scoring, consult the











Alright,vip777slotlogin… not bad at all! I really like the variety of slot games they have. I’ve hit a few small wins, so I’m happy! Might get lucky someday. vip777slotlogin
Kingjililogin made it super easy to create an account and jump into the action. No messing around. The site is fast, and it runs smoothly on my phone. Thumbs up! Head over to kingjililogin.
Been messing around on rwin99 for a few days. I actually won a bit on their sports bets! The odds aren’t always the best, but they cover a lot of different sports. If you like betting on sports, give rwin99 a shot.
Hey, check out P898, it’s pretty cool, lots of fun games that i have not seen before. If you’re looking for a new website go check out p898!
Just won a bunch of money on PH898! Maybe you should check it out. Some of the games are crazy easy to win! get in on that action! here the site: ph898
Okay, weatistheph90… the name’s a mouthful! But what IS it? Anyone got the lowdown? Lay it on me!
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.