Date: January 21, 2026, Tags: #CyberSecurity #Cloudflare #ACME #SSL #ZeroDay #DevOps In the last decade, the web moved almost exclusively to HTTPS. This massive shift
Author: U Debasish Rao
CVE-2025-55182: 7 Critical Insights Into the React Server Components RCE
CVE-2025-55182 is a critical pre-authentication remote code execution (RCE) vulnerability in React Server Components (RSC), impacting production deployments of React 19 that rely on Server
7 Powerful OWASP Authentication Failures
OWASP Authentication Failures remain the leading cause of breaches across web apps, mobile apps, APIs, cloud systems, and microservices. This extended edition (3000+ words) covers
TLS Handshake in Secure Communication: How It Protects the Internet
Transport Layer Security (TLS) stands as a cornerstone of modern internet security, a protocol meticulously designed to ensure privacy and data integrity across digital communications.
How to Create a Self-Signed SSL Certificate for Nginx on Linux
Why You Need a Self-Signed Certificate (and When Not To) Creating a self-signed SSL certificate for Nginx on Linux is a quick way to enable
AI in Cyberattacks: How Artificial Intelligence Is Powering Modern Threats
AI in cyberattacks is no longer science fiction — it’s a rapidly growing threat where artificial intelligence is used to automate, scale, and amplify cybercrime.In
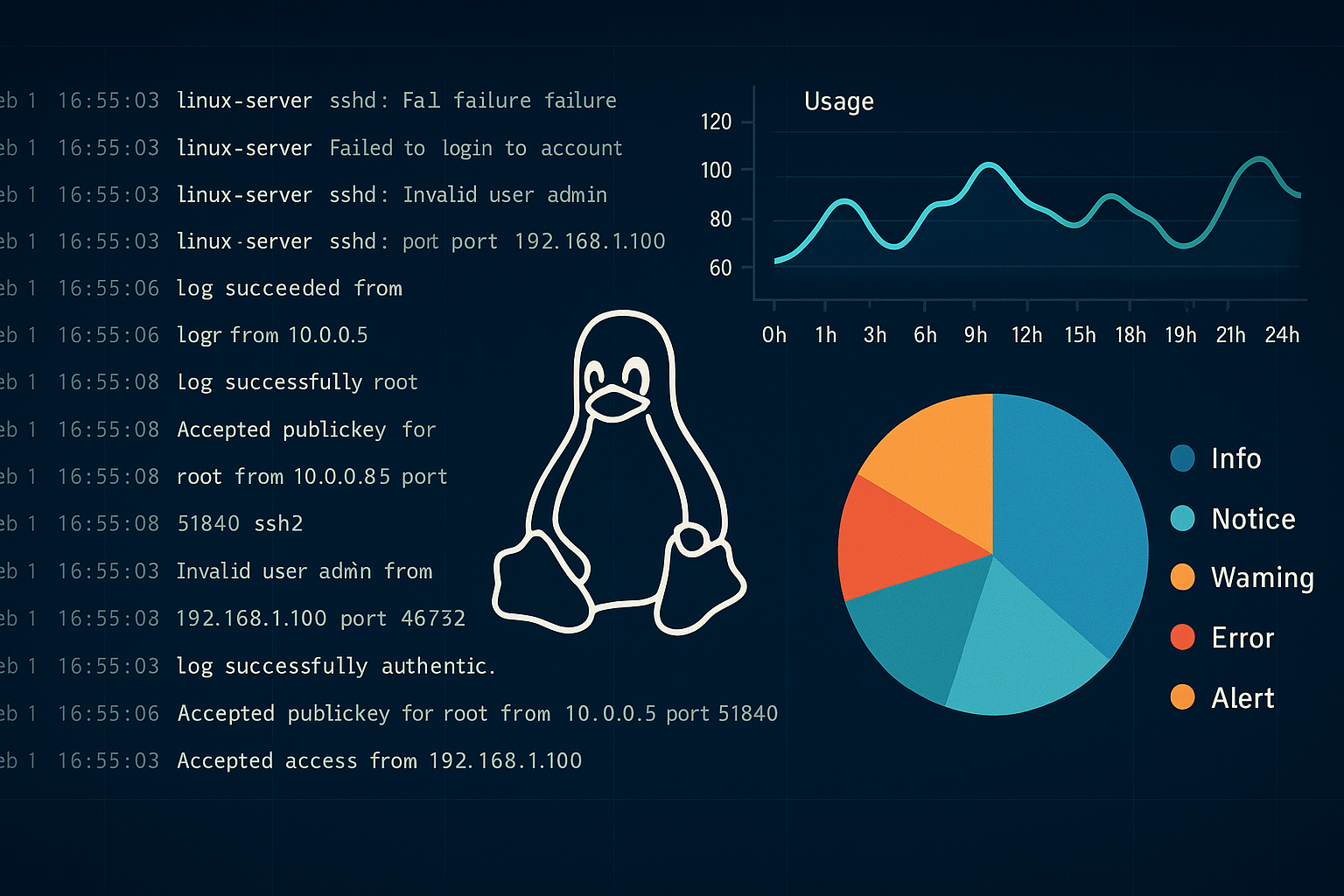
Mastering Linux Log Monitoring for SOC: A Powerful Guide to Security & Compliance
Linux log monitoring for SOC teams is a critical practice in modern cybersecurity. Think of your Linux servers as tireless digital detectives — constantly capturing
Azure Elasticsearch Service Comparison: Azure AI Search vs Fabric vs ADX
Managing vast datasets often demands capabilities similar to Elasticsearch for robust search and real-time analytics. If your infrastructure is primarily on Azure, you’ll want managed