Broken access control explained — this vulnerability remains one of the most widespread and dangerous risks in modern applications. From unauthorized data access to full privilege escalation, Broken Access Control continues to dominate OWASP Top 10 reports and real-world breach data.
In this guide, we break down what makes it so severe, how attackers exploit it, and the 7 critical failures you must fix immediately.
Also read:
👉 OWASP Top 10 2025 Release Candidate
https://hackervault.tech/owasp-top-10-2025-release-candidate/
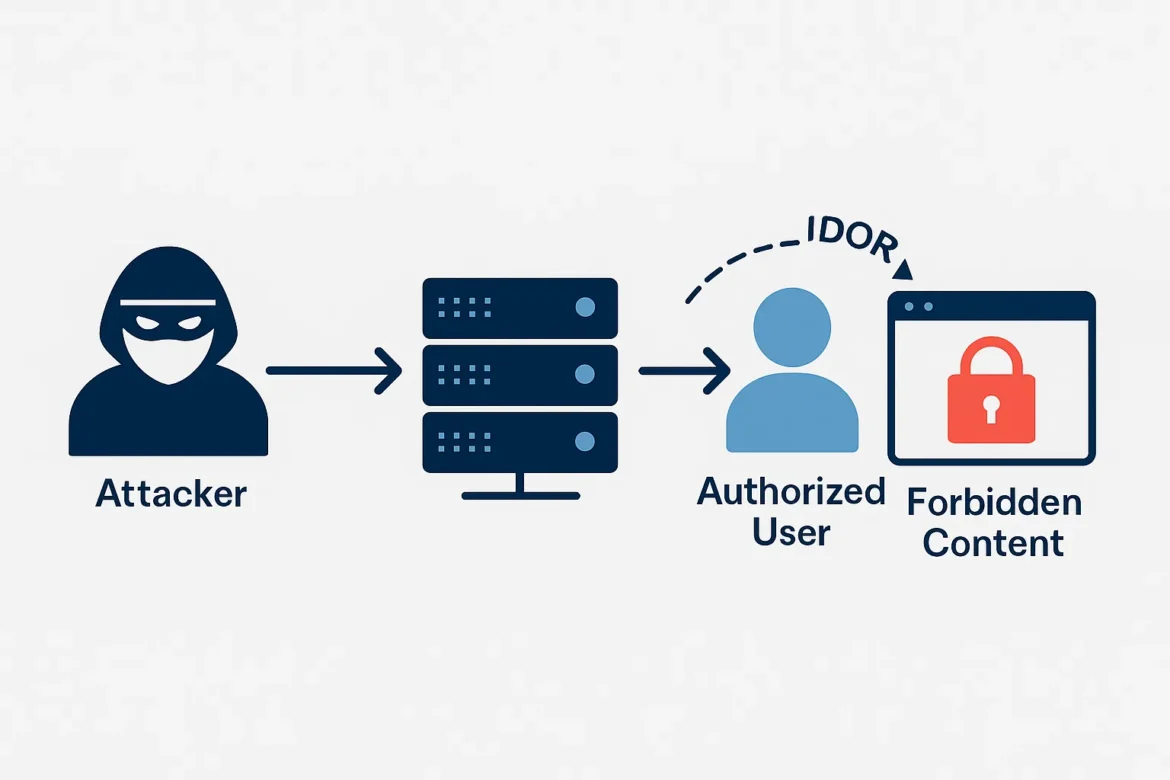
🧩 1. What Is Broken Access Control?
Access control ensures that users can only perform actions they are authorized for.
When these controls fail, attackers can:
- Access other users’ data
- Modify sensitive information
- Escalate privileges
- Access admin-only functions
- Exploit hidden or deprecated endpoints
Unlike technical bugs, these are usually logic flaws — making them harder to detect but extremely easy to exploit.
⚠️ 2. Why Broken Access Control Is So Dangerous
Broken Access Control is consistently ranked as:
- #1 most exploited vulnerability in the world
- Present in over 70% of web apps (per OWASP reports)
- The cause of large-scale data breaches (IDOR, privilege escalation, admin takeover)
Attackers love it because it is:
- Simple to test
- High impact
- Common in APIs and microservices
- Often overlooked by developers
🔥 3. 7 Critical Broken Access Control Failures You Must Fix
Below are the most dangerous and commonly exploited failures.
1) Insecure Direct Object References (IDOR)
Example:
GET /api/user?id=105
↓ Change to
GET /api/user?id=106
If no ownership check exists → attacker sees another user’s data.
2) Privilege Escalation via Parameter Tampering
Tampering with role or permission parameters such as:
role=user → role=admin
3) Accessing Hidden or Deprecated URLs
Developers hide links but forget server-side checks:
/admin
/debug
/backup
/internal
4) Missing Authorization on API Endpoints
API v2 might enforce authorization, but API v1 or legacy endpoints might not.
5) Omission of Object-Level Access Checks
Returning data based solely on ID without validating user ownership.
6) Bypassing Access Controls with HTTP Verb Tampering
Example:
DELETE /user/20 → 403
But
POST /user/20/delete → 200
7) Forced Browsing of Restricted Resources
Users manually guessing URLs of restricted documents or admin pages.
🕵️ 4. Real-World Attack Scenarios
✔ IDOR Exploit in E-Commerce Platforms
Attackers change order IDs and retrieve invoices of other customers.
✔ Admin Panel Exposure
A hidden admin route is left unprotected:
/admin/settings
An attacker discovers and accesses it directly.
✔ API Request Replay With Modified JWT
Attackers modify JWT claims:
"role": "admin"
If backend doesn’t validate signature → full takeover.
🛡️ 5. How to Prevent Broken Access Control
1. Enforce Server-Side Authorization on Every Request
Never trust client-side UI restrictions.
2. Deny-by-Default Policies
If a role/action is not explicitly allowed → deny access.
3. Implement RBAC or ABAC
Use centralized permission checks.
4. Validate Object Ownership in APIs
Before returning user data, verify:
Does this user own this object?
5. Use Indirect References
Replace numeric IDs with UUIDs.
6. Disable Forced Browsing
Return strict 403 responses for unauthorized access.
7. Security Testing & Monitoring
Regularly use:
- Burp Suite
- OWASP ZAP
- Waf rules
- Pentesting tools
- Automated DAST
🔎 People Also Ask (PAA Section)
1) What is an example of Broken Access Control?
Accessing another user’s data by changing an ID in the URL (IDOR).
2) How serious is Broken Access Control?
It often leads to full account takeover, data leaks, or admin compromise.
3) How do you detect Broken Access Control?
Manual testing, Burp Suite, fuzzing, and permission-based pentesting.
❓ FAQ SectionQ1: What is broken access control explained simply?
Broken Access Control happens when an attacker can perform actions or access data they’re not authorized to.
Q2: How do attackers exploit Broken Access Control?
By modifying IDs, forcing access to hidden routes, tampering with parameters, or bypassing authentication logic.
Q3: How can developers fix Broken Access Control?
By enforcing server-side authorization, validating ownership, and using deny-by-default logic.
Q4: Is Broken Access Control part of OWASP Top 10 2025?
Yes — it remains one of the most critical and exploited risks.
📌 Conclusion & CTA
Broken access control explained — this vulnerability remains the #1 most exploited security flaw across web applications, APIs, and microservices. By understanding how attackers exploit access control logic and applying strong authorization checks, developers can eliminate entire classes of high-risk vulnerabilities.










Okay, the name’s a bit weird, right? 98winfarter…but the site itself is decent. Don’t let the name put you off. Some interesting games on there. Give 98winfarter a peek, you might be surprised.
Interesting article! Bankroll management is key, and responsible gaming platforms like scatter link slot download are crucial for a safe experience. Diversifying your game selection is also smart!
Looking for some new games and found gamespk. Lots of options to choose from, pretty good resource. Have a look: gamespk
Just stumbled on m666. Not bad! Seems like a solid resource. Will definitely be back to see what else they’ve got. Explore at m666!
Mafia777pk is where it’s at! Big wins, good times. Definitely recommend if you’re lookin’ for some excitement. Don’t be a chump, check it out! mafia777pk
Downloaded the 88betapps app the other day. Pretty slick, to be honest. Easy to use and had a good selection of games. Worth a look if you’re on the move a lot. Cheers!88betapps
Sup guys! I’ve been playing at mansionm88 for a while now and have had a good experience. Plenty of games and they seem to payout winnings fairly quickly. Definitely one of the better ones.
Downloaded the Hz88app and it’s surprisingly good. Runs smooth and the games are engaging. If you’re looking for a new app to try, hit up hz88app, you wont be disappointed!
3win88 has been throwing up a lot of ads online. Is it as good as the ads make it out to be? Want honest opinions before I dive in. Show me what you know: 3win88
Alright, folks! Just checked out fk88betvn. Seems like a decent spot to try your luck. Give it a whirl and see what you think! Check it out here: fk88betvn!
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article. https://accounts.binance.info/en-IN/register-person?ref=A80YTPZ1
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me?
Your article helped me a lot, is there any more related content? Thanks! https://www.binance.info/register?ref=IHJUI7TF
Your point of view caught my eye and was very interesting. Thanks. I have a question for you. https://www.binance.com/ph/register?ref=IU36GZC4
Alright folks, phpark369login is where it’s at. Smooth login process, no drama. Give it a shot and let me know what you think. It’s making things easy for me! phpark369login
Hey there, I stumbled upon pr33win and I’m giving it a thumbs up. Good stuff happening there. Worth checking out if you wanna try your luck. pr33win
Yo gamers, need some fire games? vipgamedownload is the place. Found some cool stuff there myself. Get your download on! vipgamedownload
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.
Your point of view caught my eye and was very interesting. Thanks. I have a question for you. https://accounts.binance.info/register-person?ref=JW3W4Y3A