OpenAI Mixpanel Incident: On November 9, 2025, OpenAI disclosed a security incident — but not inside their own systems.The issue originated from Mixpanel, one of
Tag: Cybersecurity
OWASP Top 10 2025: What’s New, Changed & Security Guide
🔍 Introduction Every few years, OWASP publishes the Top 10 list — the world’s most trusted benchmark of web-application security risks.The 2025 Release Candidate (RC1)
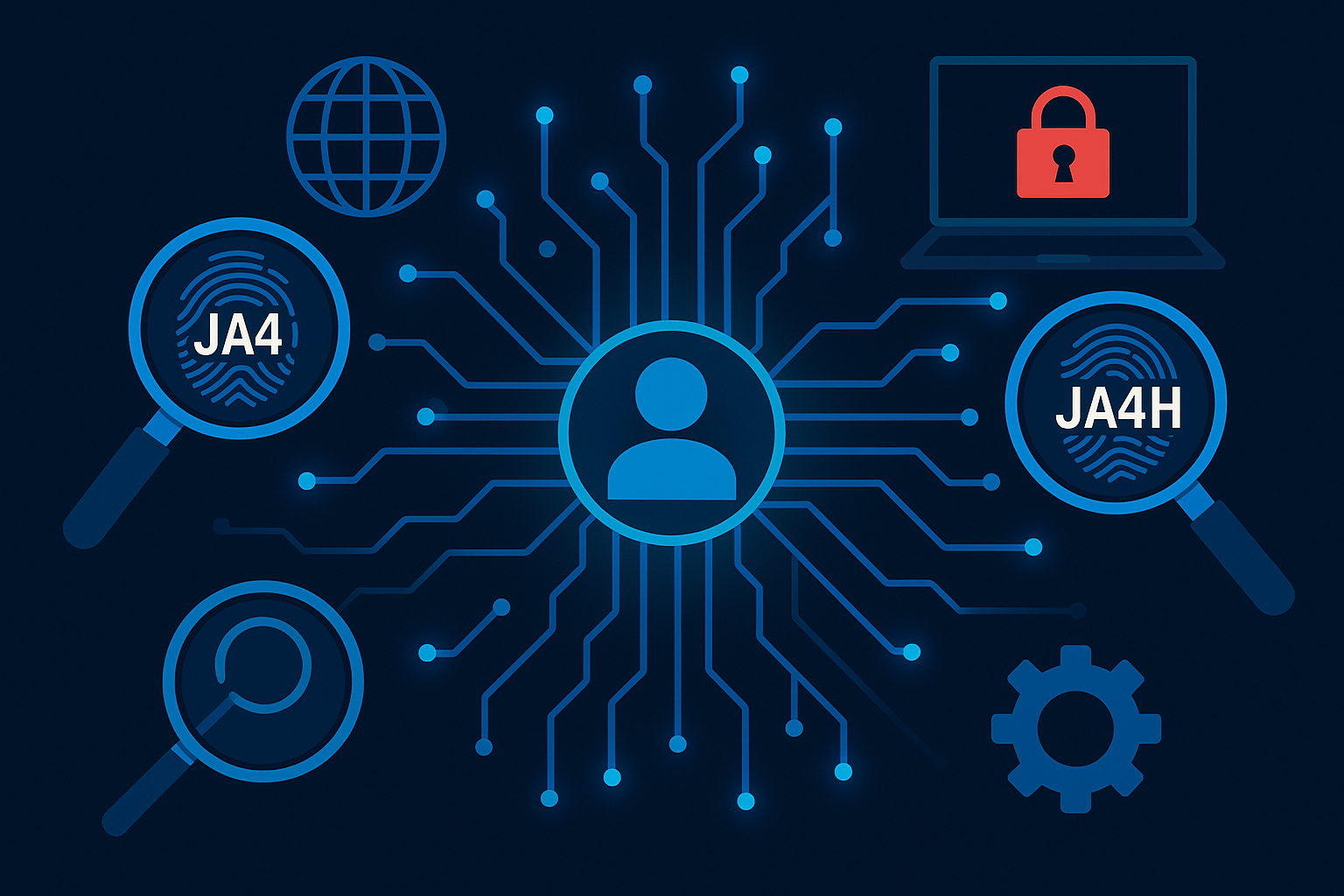
How Does JA4/JA4H Analyze Client Architecture for WAF Detection?
Client Architecture in JA4/JA4H WAF Detection plays a crucial role in understanding the true nature of the device connecting to your web applications. JA4 and
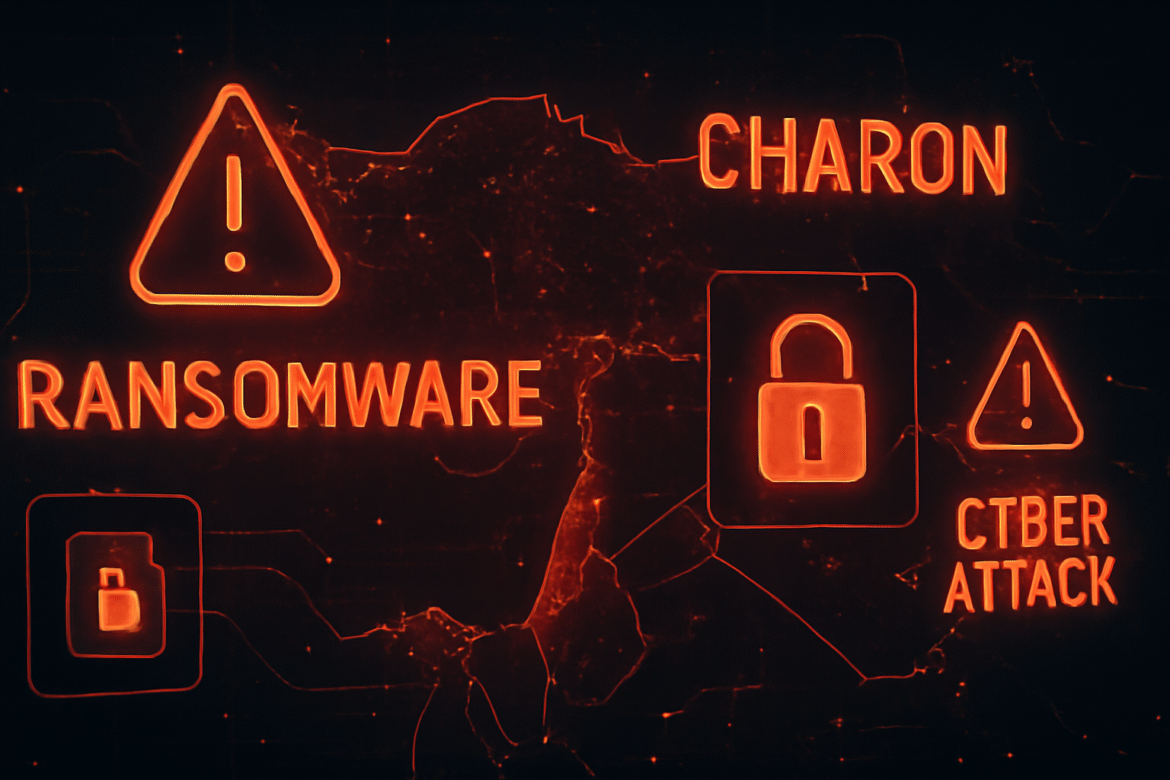
Charon Ransomware Strikes Middle East: A New Era of APT-Level Ransomware Attacks
In August 2025, the Charon ransomware attack has been detected targeting critical sectors across the Middle East, marking a new phase of sophisticated ransomware blending
TLS Handshake in Secure Communication: How It Protects the Internet
Transport Layer Security (TLS) stands as a cornerstone of modern internet security, a protocol meticulously designed to ensure privacy and data integrity across digital communications.
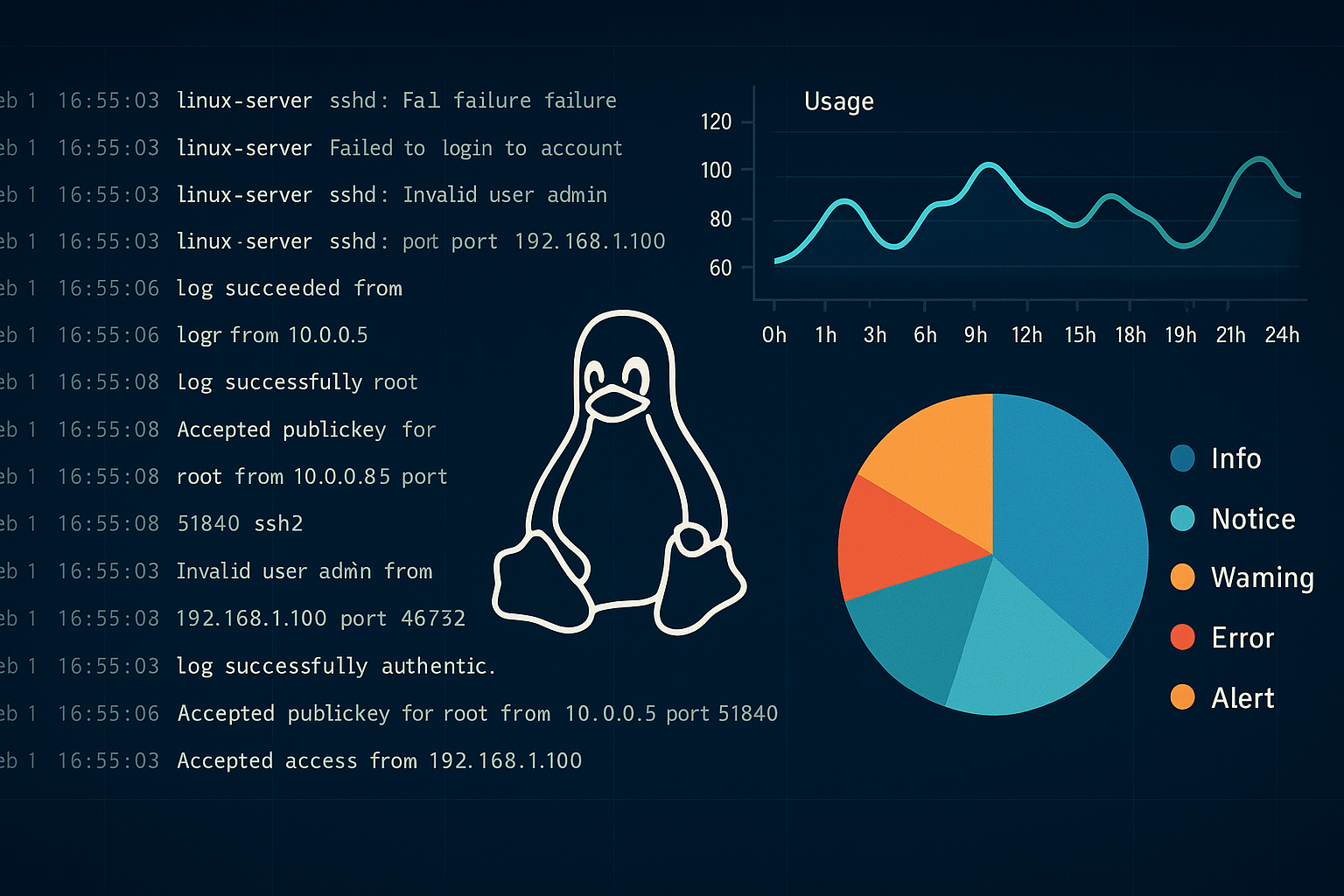
Mastering Linux Log Monitoring for SOC: A Powerful Guide to Security & Compliance
Linux log monitoring for SOC teams is a critical practice in modern cybersecurity. Think of your Linux servers as tireless digital detectives — constantly capturing
CVE Program Expiration Crisis Averted: What It Means for Global Cybersecurity
CVE program expiration in April 2025, the cybersecurity community came dangerously close to losing a fundamental piece of its global infrastructure: the CVE (Common Vulnerabilities
SQL Injection (SQLi) – The Classic Web Vulnerability Still Haunting the Internet
SQL Injection is a web security vulnerability that allows an attacker to interfere with the queries that an application makes to its database. It can
Building Your First Line of Defense: A Practical Guide to Defensive Security
Defensive security refers to the proactive strategies and technologies that protect systems, networks, and data from cyber threats. Unlike offensive security (e.g., penetration testing), the
Inside Malware: How to Detect, Dissect & Defend Against Hidden Cyber Threats
🔍 What is Malware Analysis? Malware analysis is the methodical process of dissecting malicious software to understand its behavior, origin, impact, and detection mechanisms. It’s