In August 2025, the Charon ransomware attack has been detected targeting critical sectors across the Middle East, marking a new phase of sophisticated ransomware blending
Category: Threat Inteligence
AI in Cyberattacks: How Artificial Intelligence Is Powering Modern Threats
AI in cyberattacks is no longer science fiction — it’s a rapidly growing threat where artificial intelligence is used to automate, scale, and amplify cybercrime.In
Mastering Linux Log Monitoring for SOC: A Powerful Guide to Security & Compliance
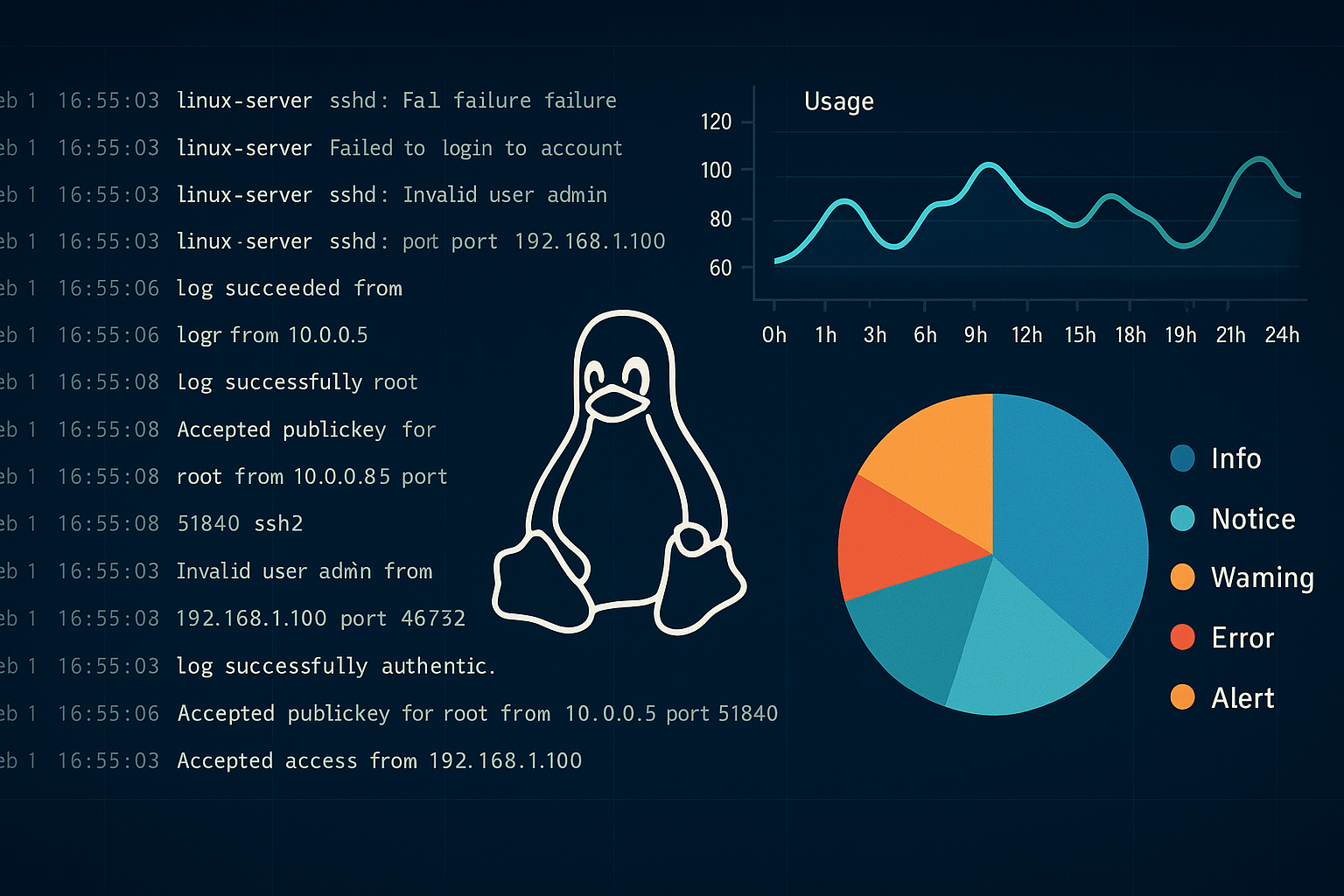
Linux log monitoring for SOC teams is a critical practice in modern cybersecurity. Think of your Linux servers as tireless digital detectives — constantly capturing
Top 5 Ways AI-Powered Cyberattacks Are Rising: A New Era of Threats
🔎 What Are AI-Powered Cyberattacks? AI-powered cyberattacks refer to malicious activities enhanced or fully driven by artificial intelligence. These attacks leverage machine learning (ML), natural
Introduction to Threat Intelligence: Staying One Step Ahead of Cyber Attacks
In today’s hyper-connected digital world, cyber attacks have become more frequent, complex, and damaging. Organizations must move beyond traditional security approaches—and that’s where Threat Intelligence