OpenAI Mixpanel Incident: On November 9, 2025, OpenAI disclosed a security incident — but not inside their own systems.The issue originated from Mixpanel, one of
Category: Case Studies
Deep dives into real-world hacks, breaches, and security incidents.
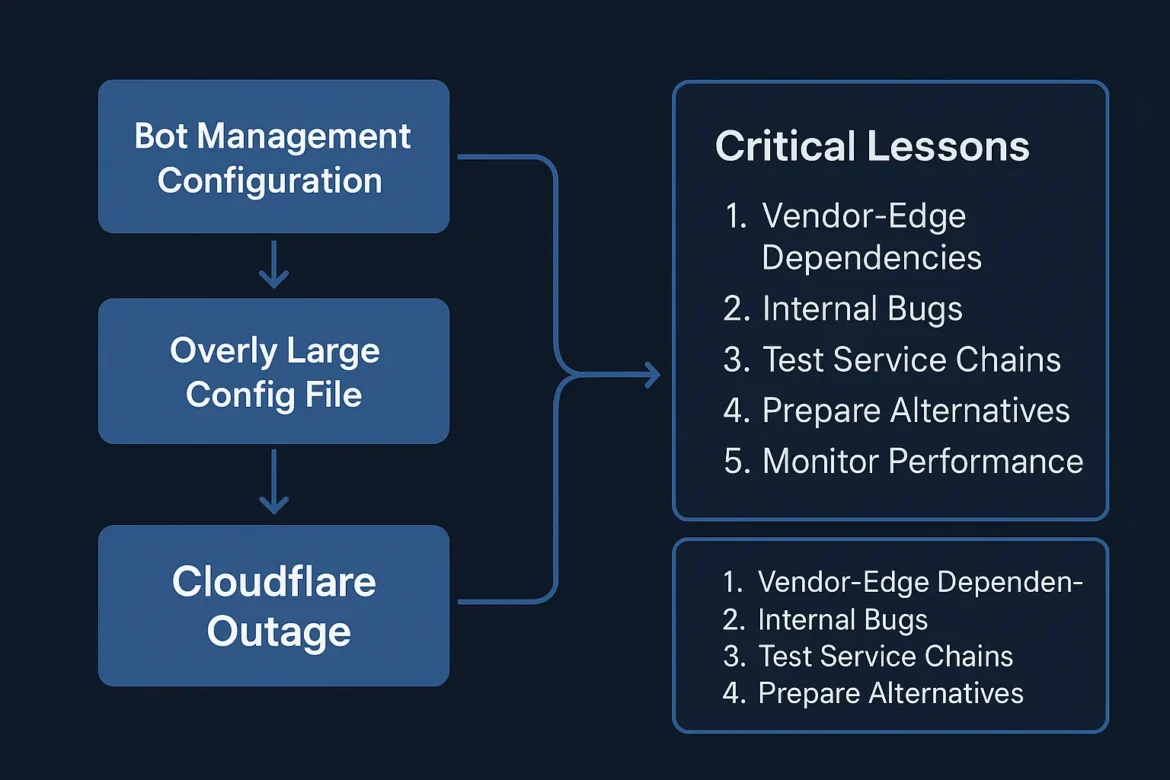
Cloudflare Outage Explained – 5 Critical Lessons
On November 18 2025, Cloudflare’s global network suffered a major outage — affecting thousands of websites, including high-profile platforms such as ChatGPT and X.Unlike many
AI in Cyberattacks: How Artificial Intelligence Is Powering Modern Threats
AI in cyberattacks is no longer science fiction — it’s a rapidly growing threat where artificial intelligence is used to automate, scale, and amplify cybercrime.In
AI Could Have Prevented This: Inside the 2025 Superannuation Cyberattack
In April 2025, a sophisticated cyberattack targeted major Australian superannuation funds including AustralianSuper, Cbus, Hostplus, Rest, and the Australian Retirement Trust. Attackers used credential stuffing,