OWASP Authentication Failures remain the leading cause of breaches across web apps, mobile apps, APIs, cloud systems, and microservices. This extended edition (3000+ words) covers
Category: Web Application Security
Research and methods for securing and attacking web apps.
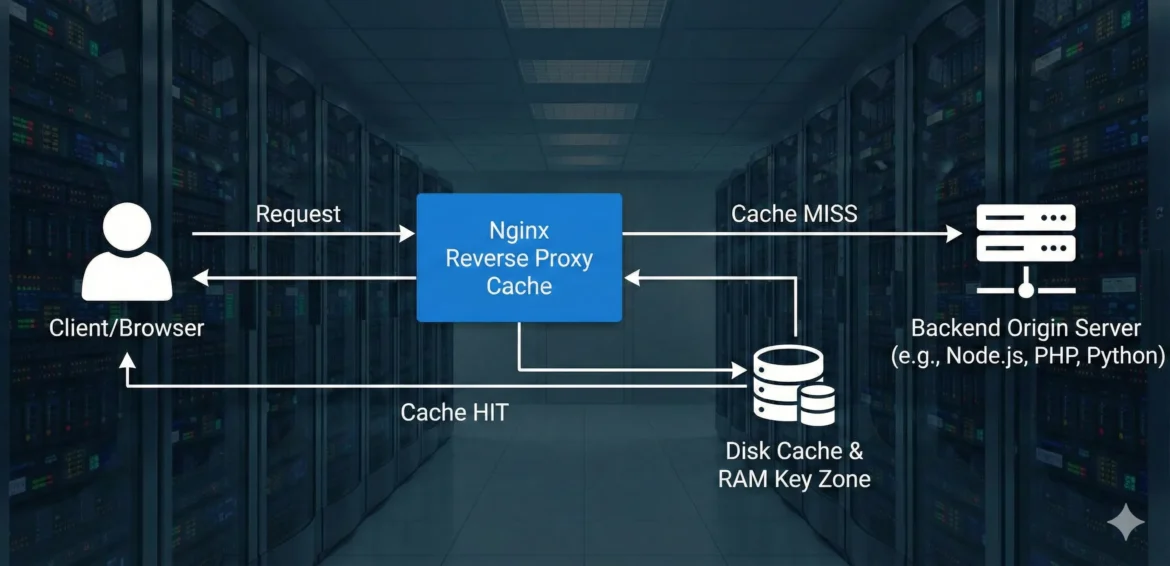
5 Powerful Nginx Caching Secrets to Drastically Boost Performance
The path to a HackerVault-grade fast and resilient web application infrastructure inevitably leads through efficient caching. And when we talk about high-performance web serving, Nginx
7 Powerful Ways to Prevent Cryptographic Failures
Cryptographic failures remain one of the most critical risks in modern security systems. In fact, the exact focus keyword cryptographic failures appears as the second
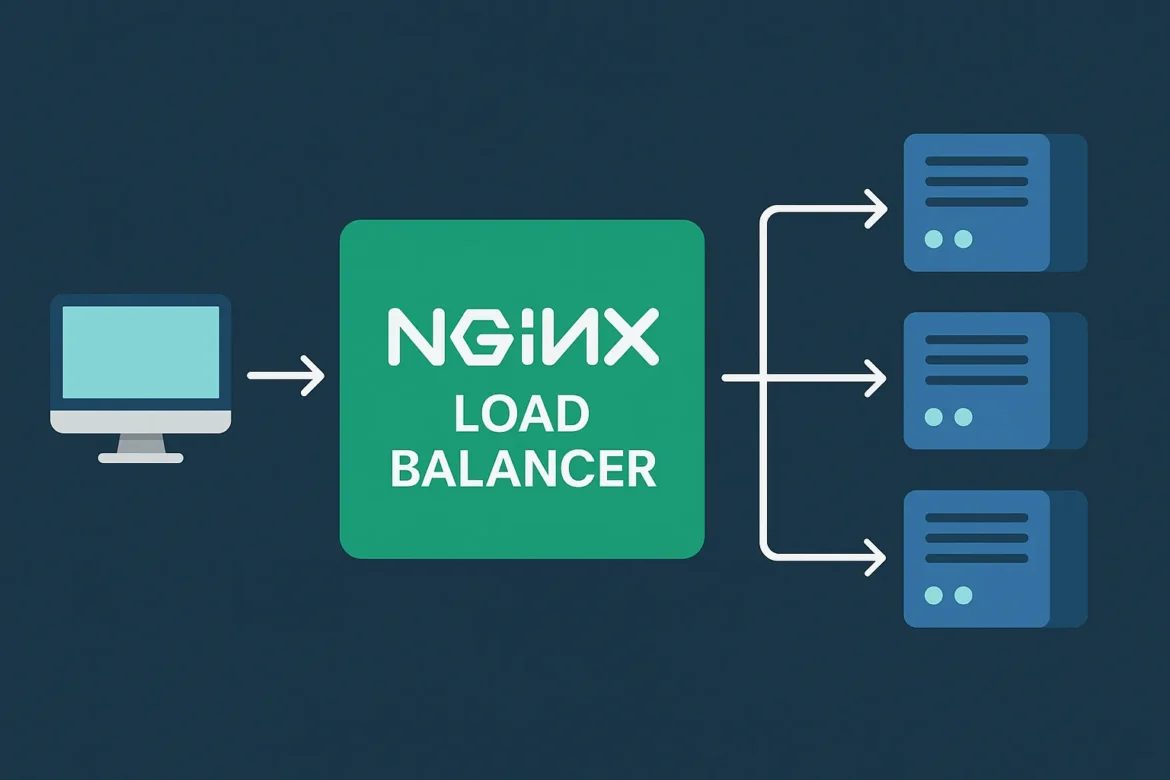
Nginx Load Balancer Guide – 5 Powerful Techniques to Boost Speed, Reliability & Security
Nginx load balancer is one of the most important components in modern web infrastructure. As applications scale across microservices, containers, and multi-node backends, Nginx remains
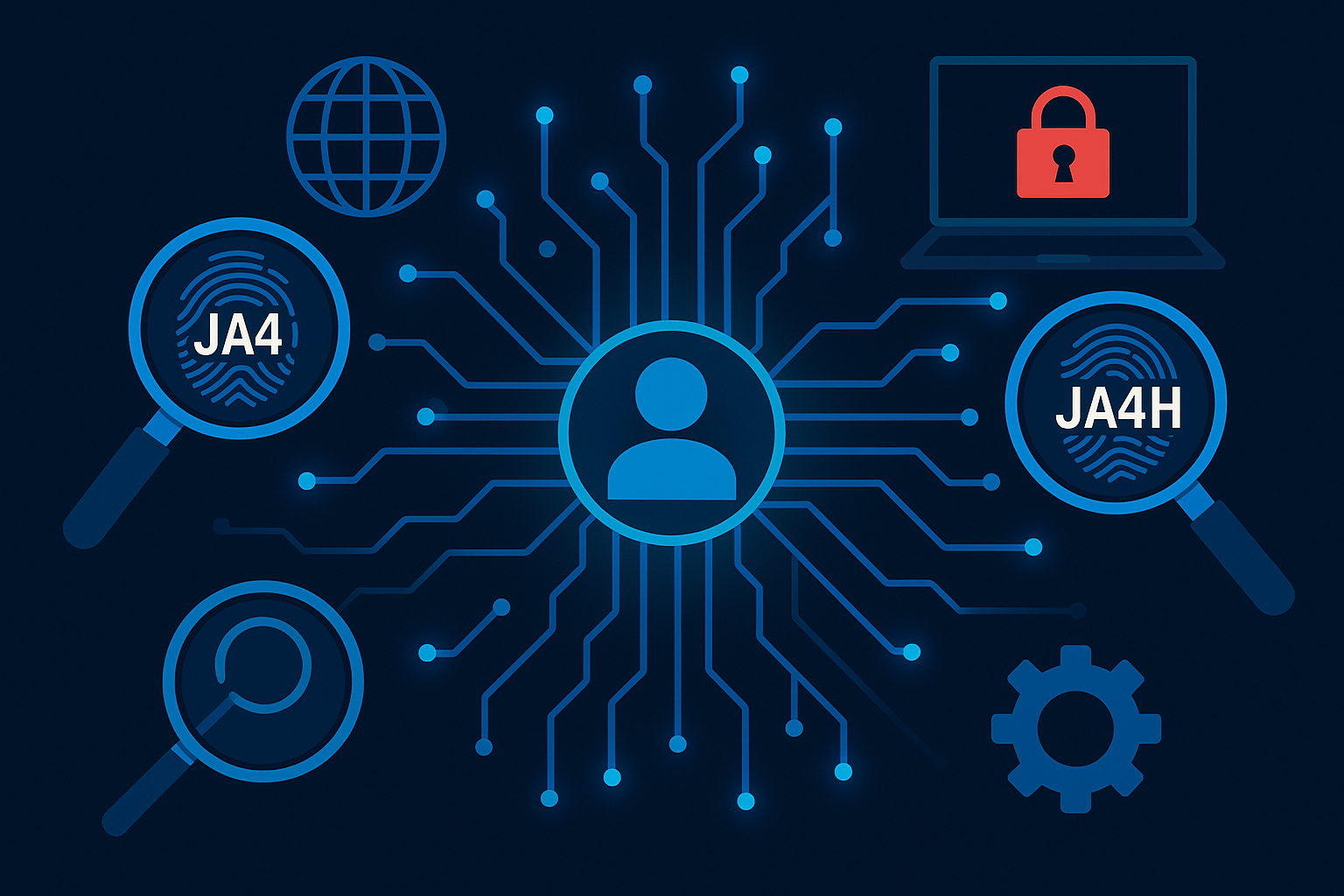
How Does JA4/JA4H Analyze Client Architecture for WAF Detection?
Client Architecture in JA4/JA4H WAF Detection plays a crucial role in understanding the true nature of the device connecting to your web applications. JA4 and
⚠️ Understanding Cross-Site Scripting (XSS): A Deep Dive into One of the Web’s Oldest Threats
🔍 What is Cross-Site Scripting (XSS)? Cross-Site Scripting (XSS) is a web vulnerability that allows attackers to inject malicious scripts into web pages viewed by
SQL Injection (SQLi) – The Classic Web Vulnerability Still Haunting the Internet
SQL Injection is a web security vulnerability that allows an attacker to interfere with the queries that an application makes to its database. It can
CVE-2025-29927: Critical Authorization Bypass in Next.js Middleware
On March 21, 2025, a critical vulnerability identified as CVE-2025-29927 was disclosed in the Next.js framework. This flaw allows attackers to bypass middleware-based authorization checks
CVE-2025-23087: The Universal Node.js Vulnerability You Can’t Ignore
🧠 What Is CVE-2025-23087? CVE-2025-23087 is a high-severity vulnerability impacting all End-of-Life (EOL) Node.js versions, up to and including v17.9.1. It isn’t a single exploit,
“Top 10 Web Vulnerabilities Every Beginner Should Know (And How to Fix Them)”
Web applications are everywhere—so are the attackers targeting them. Whether you’re a web developer, ethical hacker, or just getting started with cybersecurity, understanding common web