Web Application Firewalls (WAFs) are now a core part of modern web security architecture, sitting at the HTTP edge to detect and block attacks before
Category: Tools & Scripts
Useful cybersecurity tools, custom scripts, and automation resources.
7 Powerful Ways to Prevent Cryptographic Failures
Cryptographic failures remain one of the most critical risks in modern security systems. In fact, the exact focus keyword cryptographic failures appears as the second
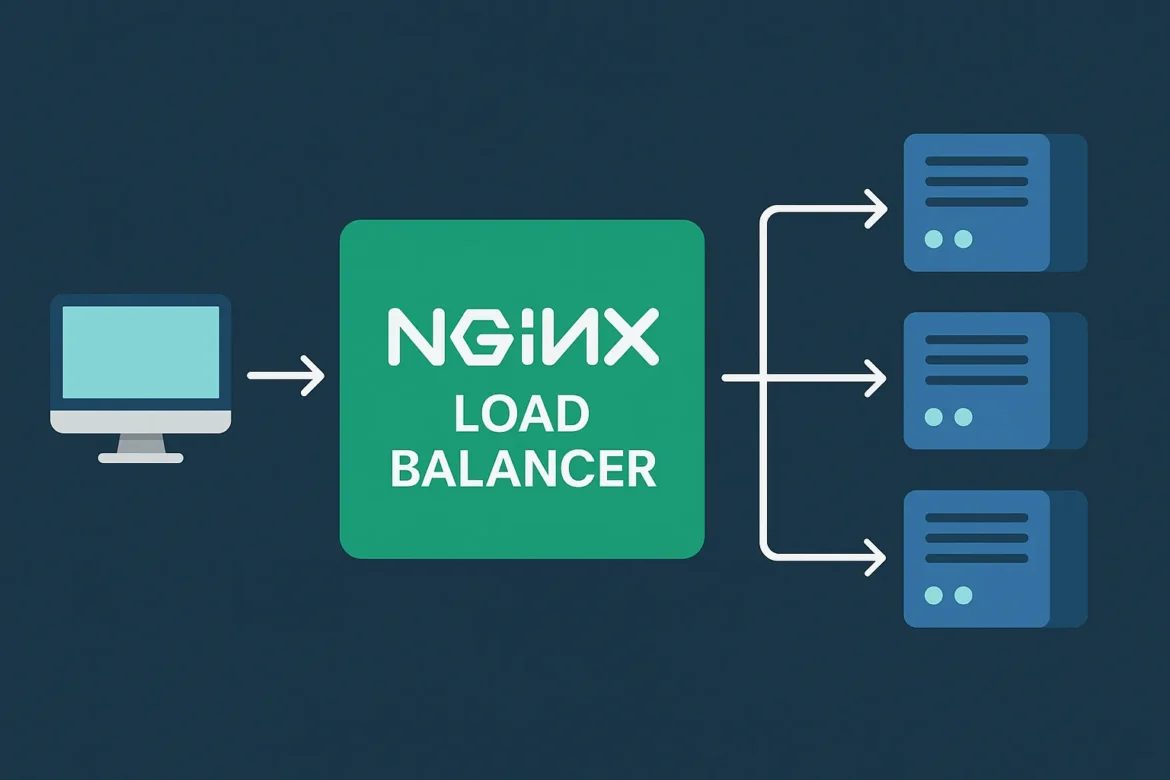
Nginx Load Balancer Guide – 5 Powerful Techniques to Boost Speed, Reliability & Security
Nginx load balancer is one of the most important components in modern web infrastructure. As applications scale across microservices, containers, and multi-node backends, Nginx remains
Nginx Reverse Proxy Guide – 5 Powerful Steps
Nginx reverse proxy guide — this feature is one of the most powerful ways to secure, optimize, and scale modern web applications. By placing Nginx
Nginx Explained: Reverse Proxy, Forward Proxy, WAF, ModSecurity & Full Functionality Guide
🔍 Introduction Nginx (engine-x) is a fast, flexible web server and proxy used for reverse proxying, SSL termination, load balancing, caching, and WAF integration. This
TLS Handshake in Secure Communication: How It Protects the Internet
Transport Layer Security (TLS) stands as a cornerstone of modern internet security, a protocol meticulously designed to ensure privacy and data integrity across digital communications.
How to Create a Self-Signed SSL Certificate for Nginx on Linux
Why You Need a Self-Signed Certificate (and When Not To) Creating a self-signed SSL certificate for Nginx on Linux is a quick way to enable
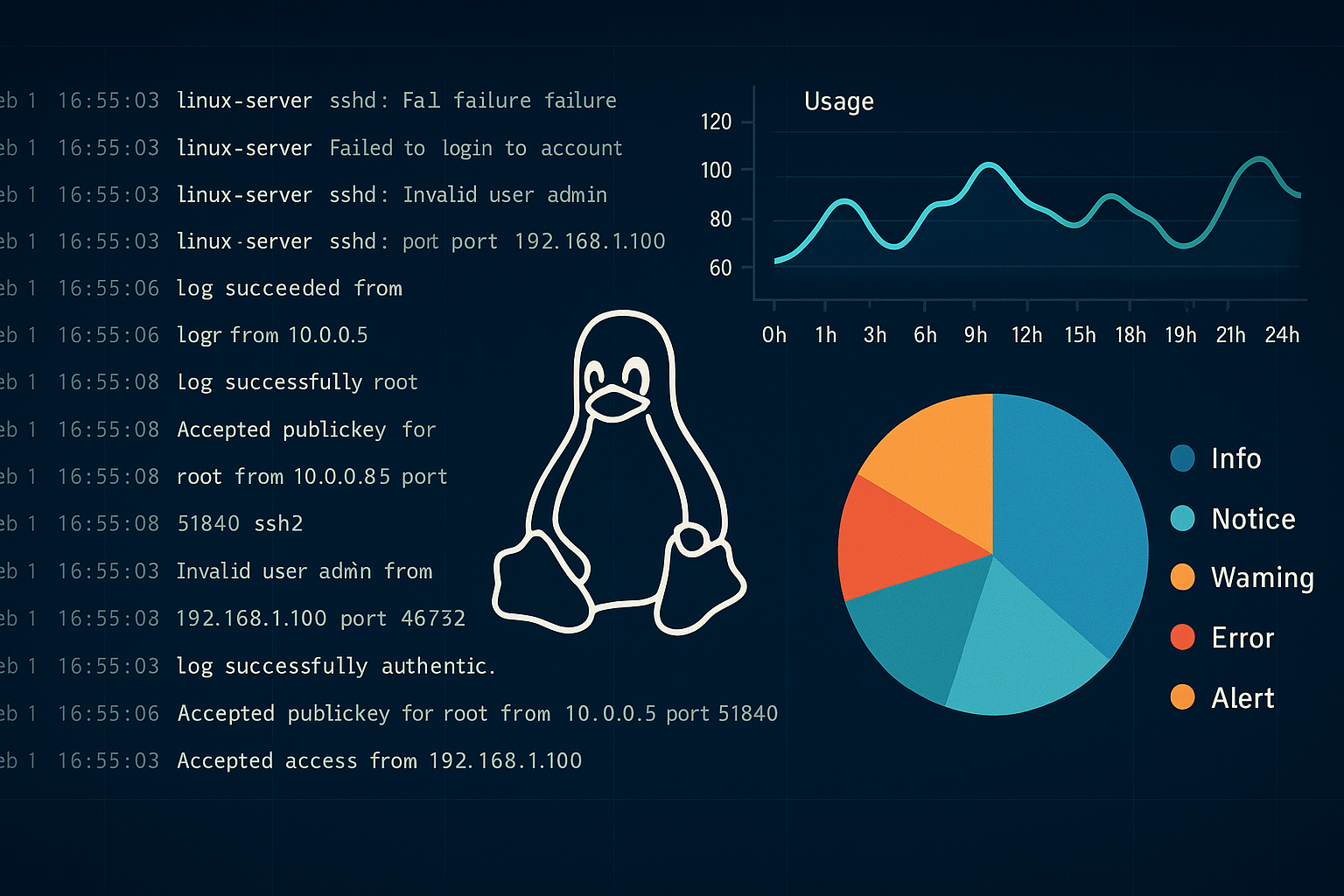
Mastering Linux Log Monitoring for SOC: A Powerful Guide to Security & Compliance
Linux log monitoring for SOC teams is a critical practice in modern cybersecurity. Think of your Linux servers as tireless digital detectives — constantly capturing
Azure Elasticsearch Service Comparison: Azure AI Search vs Fabric vs ADX
Managing vast datasets often demands capabilities similar to Elasticsearch for robust search and real-time analytics. If your infrastructure is primarily on Azure, you’ll want managed
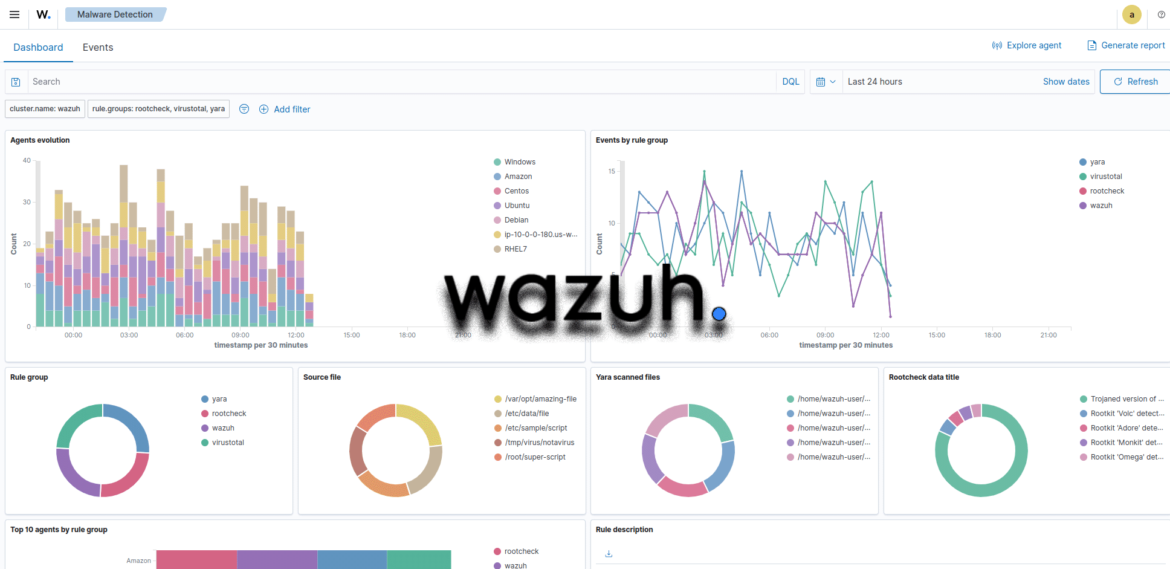
Get Ahead of Hackers with Wazuh – The Ultimate Free SIEM Tool
Wazuh is a free, open-source security platform used for threat detection, compliance monitoring, and incident response. It’s popular among security professionals because it combines powerful